In 2014, a data breach exposed information of three billion Yahoo users. In 2016, Sony Pictures employees saw sensitive private information leaked along with thousands of company documents. What do these two attacks have in common? Both started with a phishing email.
Email threats are still one of the most common ways attackers have to access sensitive information or install malware. While most known cases of phishing target anonymous users, the attackers can also use emails containing fake links or files to target specific individuals who hold sensitive information. And, as ESET researchers point out, in 2022, this kind of threat saw a year-over-year increase of almost 30%. And as AI language models make it easier to compose emails, chances are that these numbers are just about to go up even more!
Phishing attacks are a form of social engineering that makes us react with a sense of urgency and curiosity. While we can all be victims of this type of attack, we can also learn to avoid it. Let’s take a look at some real-life examples of the most common phishing used to trick us.
1. “Your session expired. Click here to sign in again.”
Some of the most common phishing lines and tactics just briefly inform you that you’ve been logged out of an account and it pushes you to fill in your credentials. Clicking the link will take you to a website looking very similar to the real one. The difference, however, is that inputting your credentials will send them right away to the attackers, who will then use them to access your information. In some instances, they might even log in for you and change the password to avoid giving you access.
This technique relies on the users’ habit of responding to such messages automatically without thinking about the content or without checking for the typical signs of a phishing email/message. (Learn about those signs here).
For example, last year, GitHub Security warned about emails impersonating the popular software development CI/CD platform CircleCI. The impersonators would send an alert with “session expired” and request a new login using GitHub credentials. “We have noticed some unusual activity on your account. Please verify.”
With this trick, scammers try to whip up a sense of urgency. Who wouldn’t want to avoid the sudden loss of an account, right? Usually, these emails impersonate messages from legitimate services such as Amazon, PayPal, etc.
For example, in late 2018, The United States Federal Trade Commission (FTC) issued a warning about phishing emails impersonating the streaming giant Netflix. These emails claimed that an account was put on hold due to something wrong with payment details, asking people to update their billing information using an embedded link, which was, of course, malicious and used to obtain login credentials.
Similarly, Apple customers were targeted in 2016 when scammers tried to steal their personal information with phishing emails claiming that users needed to reconfirm their account details because “a virus” had been found in Apple’s iTunes database.
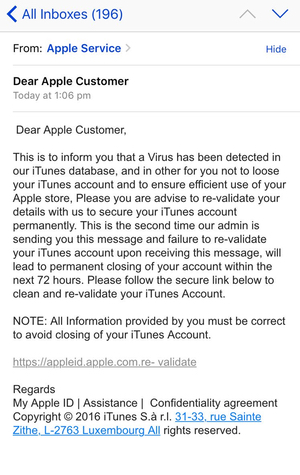
Spammed-out email
2. “I need you to make an urgent payment”
Impersonating corporate email accounts has been a long-time champion among spearphishing campaigns that don’t target anonymous people but instead go after one specific person or a group of employees in a selected company.
Before sending these fraudulent emails, scammers learn as much as possible about corporate structures, visuals, language, etc. of a business, to make the phishing email almost indistinguishable from a genuine one.
Some of these emails specifically target employees who are responsible for cash handling and financial matters. They pretend to be the CEO or a different superior authorized to order a monetary transfer and ask the victim to send funds to a specific account, supposedly the CEO’s, or maybe the company’s.
In 2018, CEO impersonation was used to steal over CA$100,000 from the Canadian city of Ottawa. Impersonating a request from the city manager, the city treasurer received a fake email to transfer the amount that ended up in the pockets of fraudsters.
Greedy scammers also tried to deceive the treasurer for a second time, but when receiving another email, the city manager was there to personally witness it. After asking whether the request was legitimate, the scam was revealed, and the crooks were caught in a lie.
3. “Dear applicant…”
These phishing emails or messages rely on fake job offers as the lure. They may trick potential victims into clicking on a phishing link or opening malicious files sent along with an email message, asking the victim, for example, to create an account and input their personal details as a means to apply for the job.
For instance, the Lazarus threat group has run numerous such campaigns, such as Operation DreamJob, discovered by ESET researchers just recently, which lured its victims with fake job offers.
These scams also exist on popular job advertising boards, so always try to verify whether the headhunter who contacted you or the job offer you see is legitimate.
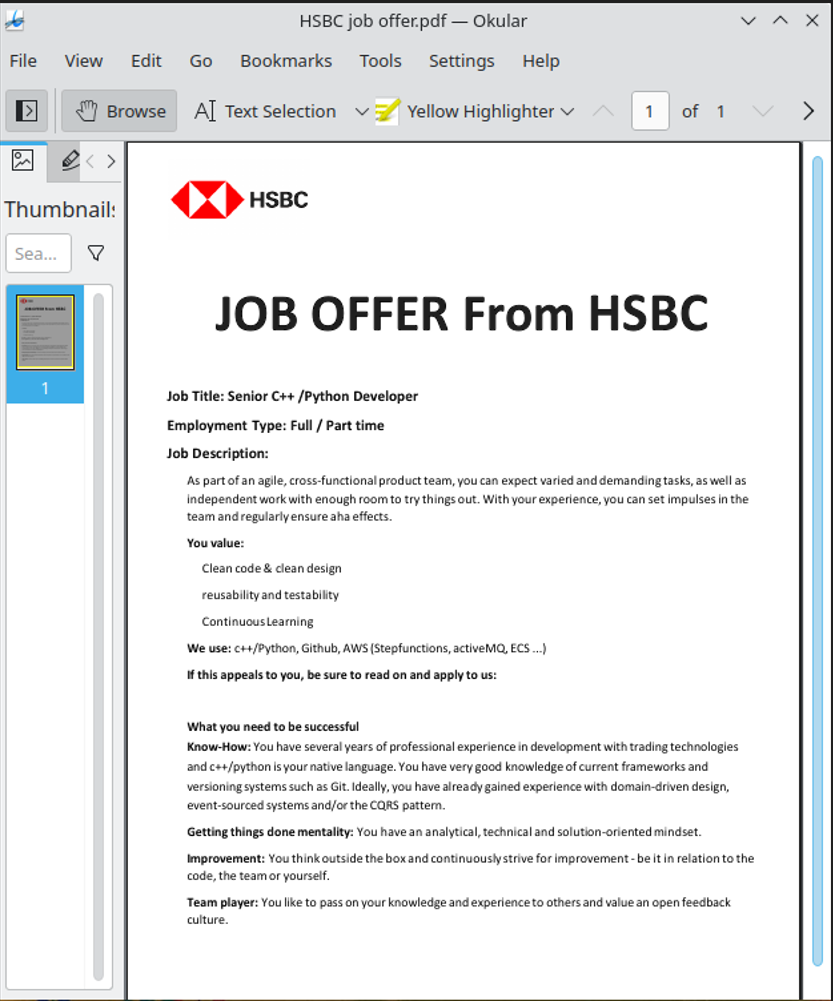
The latest campaign targeted Linux users with a ZIP file that delivers a fake HSBC job offer as a decoy.
4. “Due to the current situation… “
Phishing is also on the rise in times of big events – be it a sports event or a humanitarian crisis.
For example, at the beginning of 2023, the threat group Fancy Bear ran an email campaign related to the war in Ukraine. The emails were carrying a malicious RTF file called “Nuclear Terrorism A Very Real Threat.” Once open, it would not only compromise that computer, but it was also a blog by the reputable think tank Atlantic Council stating that the likelihood of Putin using nuclear weapons in the war in Ukraine is very low – the exact opposite of the claim in the document name and that prompted the victims to open it.
5. “Merry Christmas!”
Scams during holidays often abuse the shopping spree with emails impersonating messages from legitimate vendors. Emails contain “too-good-to-be-true” offers or create a false sense of urgency to catch the last-minute deal!
Another approach for scammers is to send emails with malicious files related to holidays, including Christmas cards, gift vouchers, etc.
6. “We are unable to process your tax return”
Only a few things in this world are certain—death, taxes, and phishing emails during tax season. Because people are filing their taxes, it isn’t surprising for them to receive some email from a tax agency.
Scammers abuse this situation by sending phishing emails with fake tax agency messages. Usually, they claim that some information is missing and request additional personal or financial details.
Other emails offer a refund while asking for credit card information.
7. No response required
Some phishing emails have little to no content, luring you to open an attached file to learn more about the matter.
For example, ESET Research uncovered the malicious campaign targeting corporate networks in Spanish-speaking countries using short emails with PDF attachments in 2021.
The subject of the email can be as simple as in this case: “Services Statement Dublin”; there was no message apart from a signature and a mobile phone contact in Venezuela.
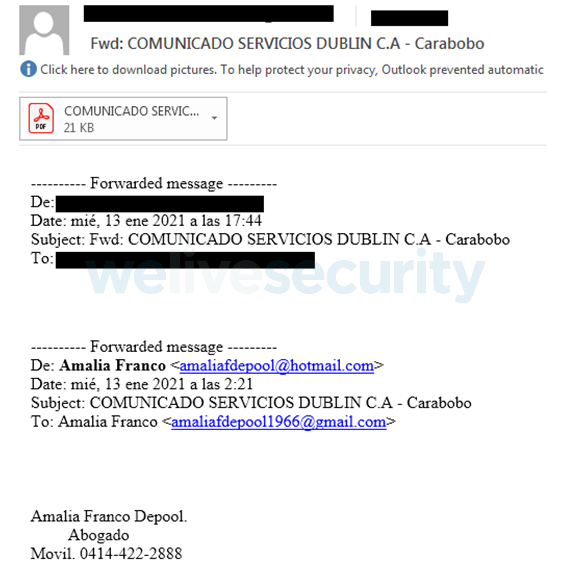
Meanwhile, the attachment is a simple PDF file with no additional informational value, but contained a link redirecting victims to cloud storage services, from which the malware could be downloaded.
How to protect against phishing emails
- Carefully read the email. Don’t click on anything automatically.
- Check whether the email address matches the real domain.
- Be cautions with unexpected sudden emails from a bank, vendor, or any other organization.
- Check the red flag, such as urgent or threatening emails requiring immediate response or requests for credentials, personal, and financial information. Numerous grammar mistakes, spelling errors, and typos are also a red flag.
- Compare the attached URL with the respective domain of a legitimate company or organization. If you spot anything suspicious, don’t click on it.
- Be aware of offers that are too good to be true and unexpected gifts.
- Don’t send money hastily. If your superior suddenly asks for such a transfer, approach them directly.
- Install a cybersecurity product with incorporated anti-phishing tools.
Phishing emails are a prevalent threat, and even IT professionals may fall for this scam. Luckily, most of those emails are quite easy to spot, if you control the urge to click links or open attachments before confirming who’s the sender.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Automotive / EVs, Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- BlockOffsets. Modernizing Environmental Offset Ownership. Access Here.
- Source: https://www.welivesecurity.com/en/scams/dear-all-what-are-some-common-subject-lines-in-phishing-emails/



