
Enterprise-managed identity and access management (IAM) enables cloud administrators to centrally configure access and security settings for the entire organization. To learn about the basics, see “How enterprise-managed IAM works.”
The case study in this blog post shows how to easily and securely implement and manage a site reliability engineering (SRE) team’s access across an enterprise.
Case study
A large banking client has a centralized site reliability engineering (SRE) team that manages operations for all resources in the organization. The client uses federation to authenticate users to IBM Cloud enterprise accounts. All teams use Kubernetes and IBM Cloud Databases resources as part of their deployment. The SRE team needs operational access to these resources for every team in every account under the company’s IBM Cloud enterprise.
As the teams introduce new resources, the SRE team manages those resources, as well. Manually managing this access setup across a growing number of accounts is error-prone, time-consuming and does not meet certain audit controls since the assigned access can be updated by the child account administrators.
By using enterprise-managed IAM templates to define access for their SRE team and assign them to the organization’s accounts, the client’s process changed from an ongoing effort to a one-time setup activity. Now, SRE access is included in both established and newly created accounts. Additionally, this access cannot be updated by the child account administrator.
In this post, we’ll provide step-by-step instructions on how to apply this solution in your organization.
Prerequisites
- Be in the root enterprise account.
- Make sure that the enterprise user performing this task has Template Administrator and Template Assignment Administrator roles on IAM services and at least the Viewer role on the Enterprise service. For more information, see “Assigning access for enterprise management.”
- Make sure that child accounts enable the enterprise-managed IAM setting. For more information, see “Opting in to enterprise-managed IAM for new and existing accounts.”
Solution
First, create a trusted profile template for the SRE team members and add access policy templates to manage all IBM Cloud Kubernetes Service clusters and IBM Cloud Databases for MongoDB instances in the child accounts. Next, assign the trusted profile template to the account group containing the account(s) to manage. Finally, we’ll grant additional access policy templates to the SRE team by creating a new trusted profile template version with the additional access required and updating the existing assignment accounts.
To implement this solution, we’ll complete the following steps:
- Create a trusted profile template.
- Add a trust relationship.
- Add access policy templates.
- Review and commit the trusted profile template.
- Assign the trusted profile template.
Then, we’ll update the assignment with these steps:
- Create a new template version.
- Add an additional access policy template.
- Review and commit the trusted profile template.
- Update the existing assignment to version 2.
Steps to create and assign a template
1. Go to Manage > Access (IAM). In the Enterprise section, click Templates > Trusted Profiles > Create. Click Create to create a trusted profile template for the SRE team:
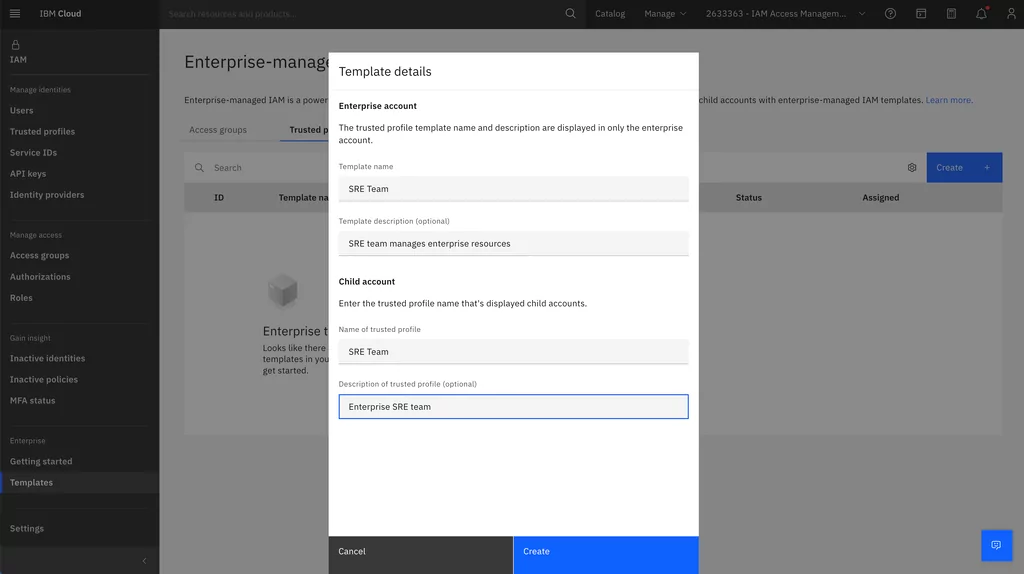 Access (IAM). In the Enterprise section, click Templates > Trusted Profiles > Create. Click Create to create a trusted profile template for the SRE team:” width=”1024″ height=”574″ lightbox=”lightbox”>
Access (IAM). In the Enterprise section, click Templates > Trusted Profiles > Create. Click Create to create a trusted profile template for the SRE team:” width=”1024″ height=”574″ lightbox=”lightbox”>2. Add a trust relationship to dynamically add the SRE team to the trusted profile based on your Identity provider (IdP):
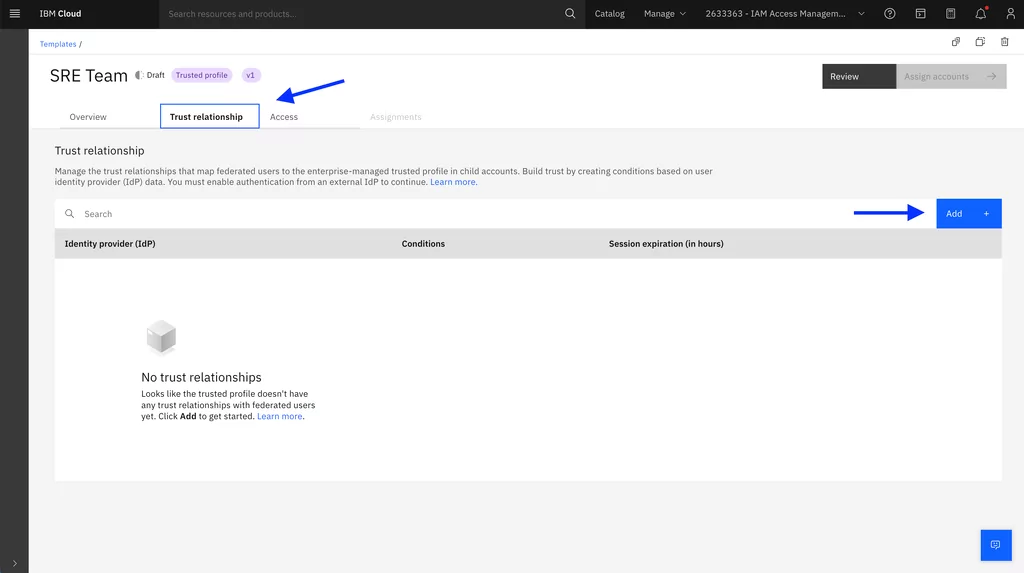
This will be based on the claims available by your IdP:
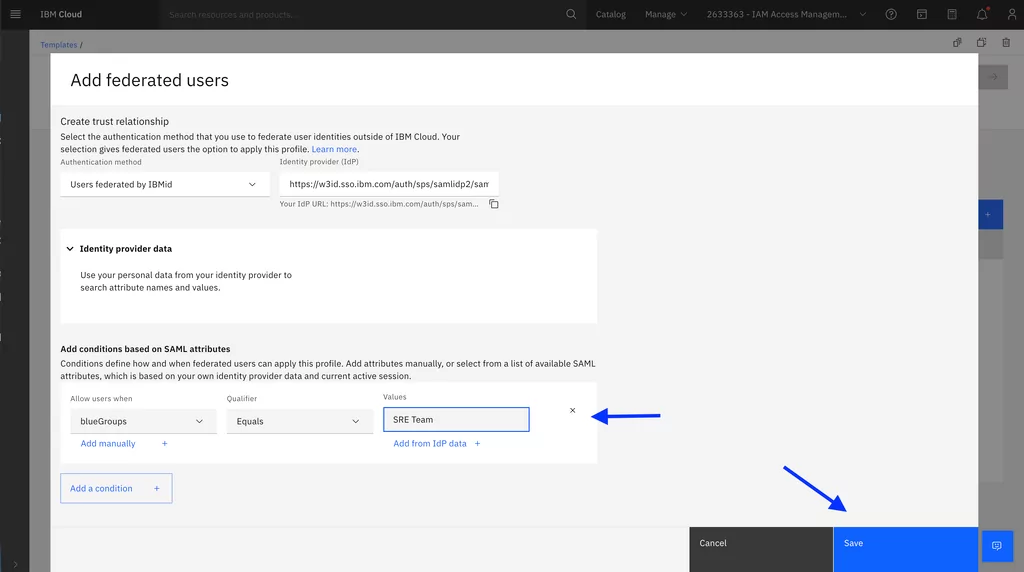
3. Go to the Access tab to create access policies:
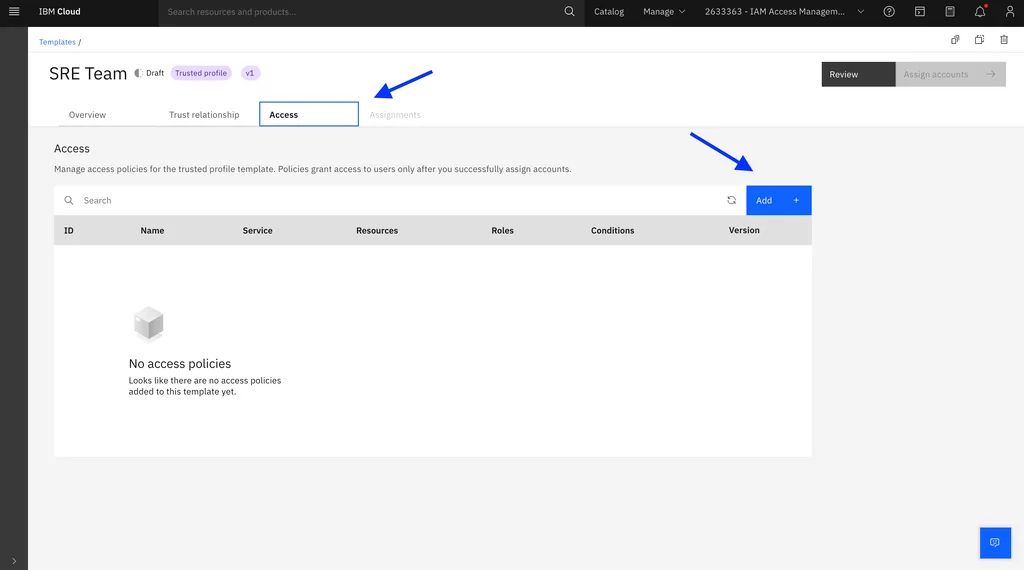
Administrator role for the IBM Cloud Kubernetes Service:
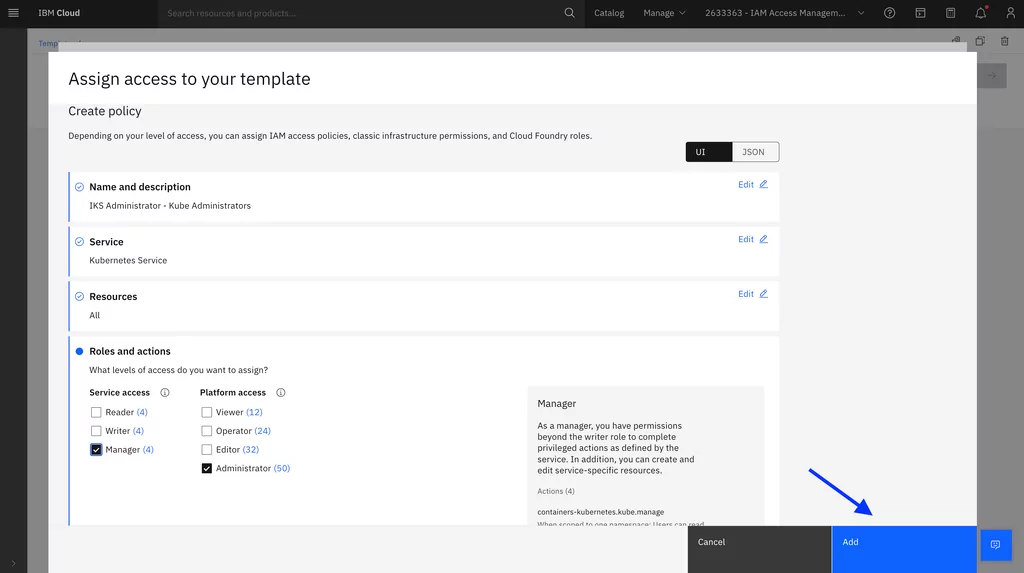
Administrator role for IBM Cloud Databases for MongoDB:
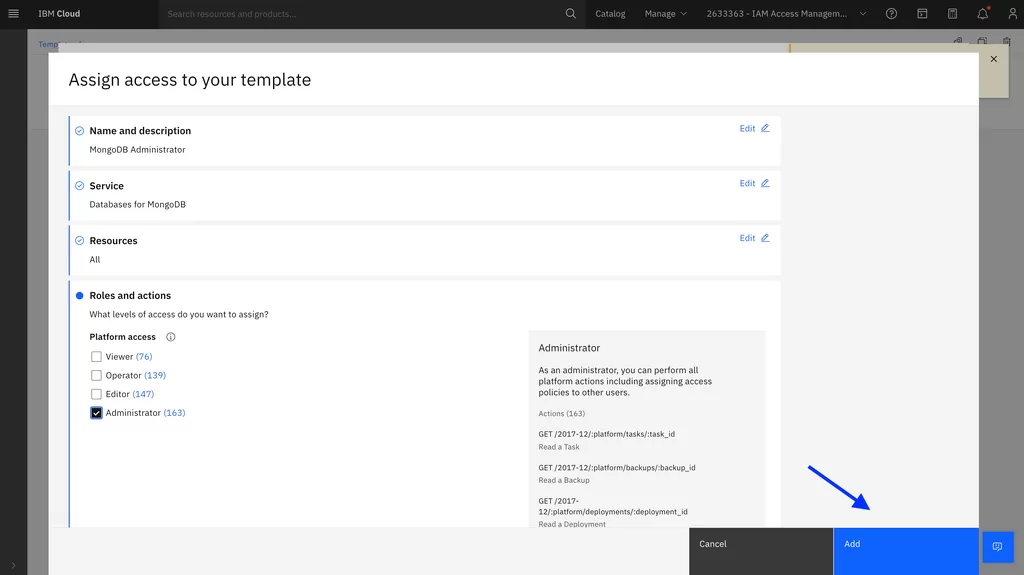
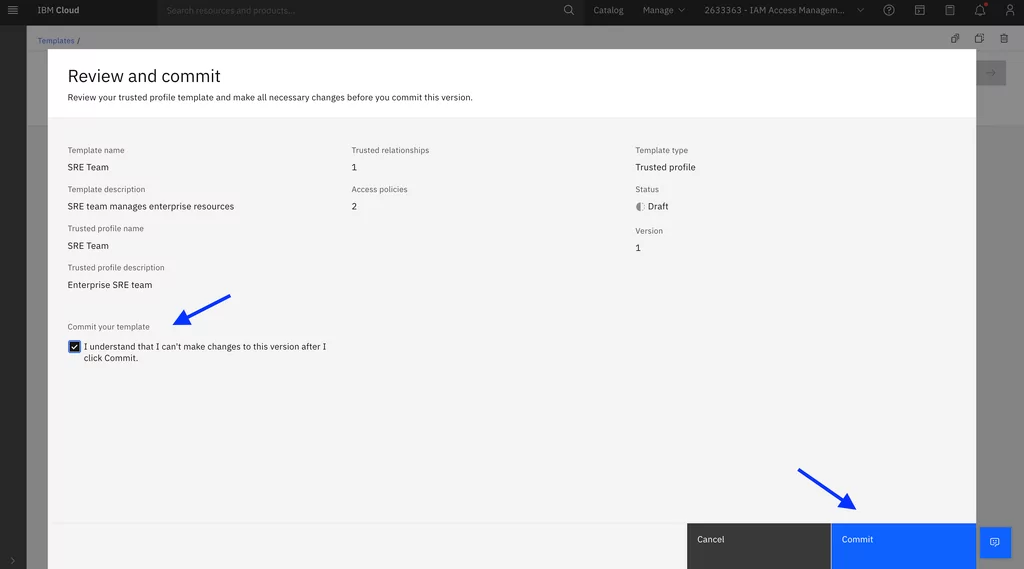
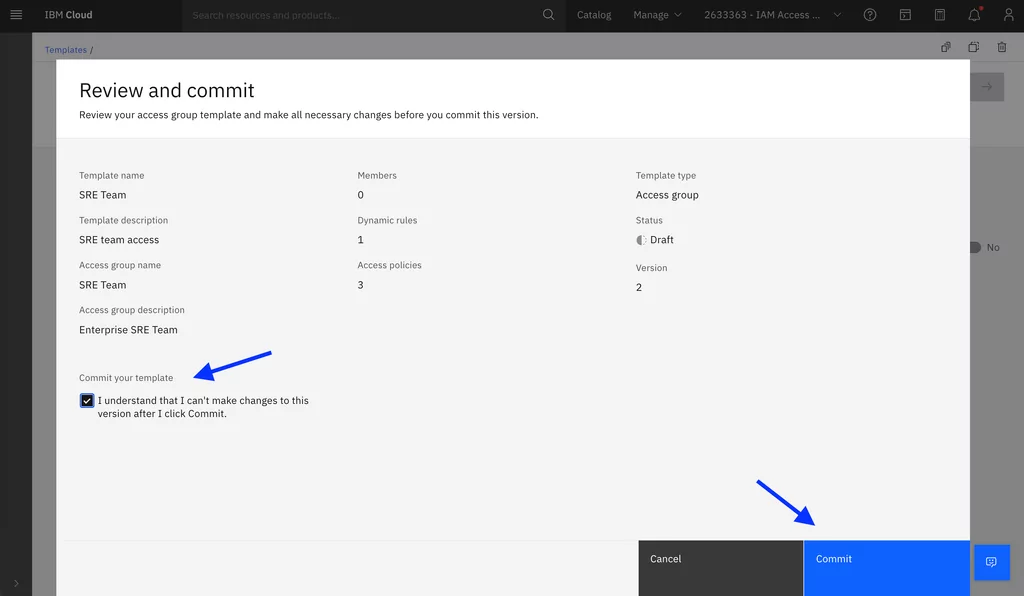
4. Review and commit the trusted profile and policies templates. Committing templates prevents them from being changed:
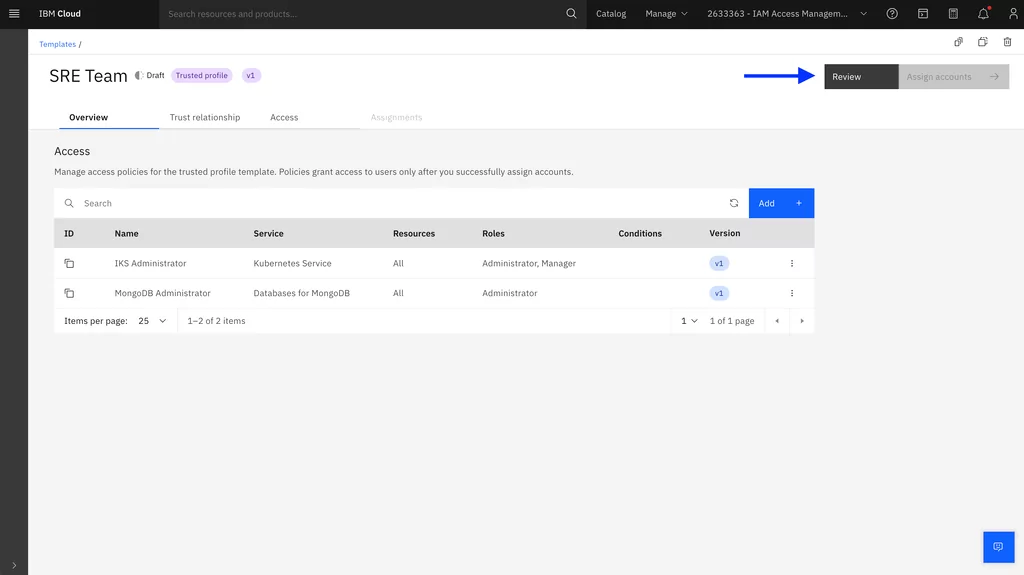
5. Assign the trusted profile template to the account group. By selecting the entire account group, the system will automatically assign templates to the new accounts when they are added or moved in:
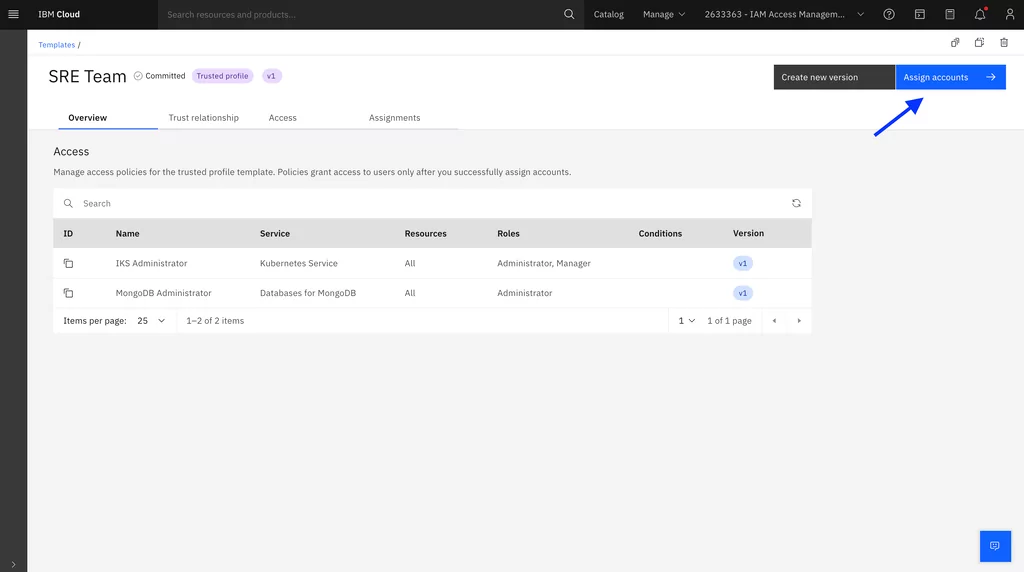
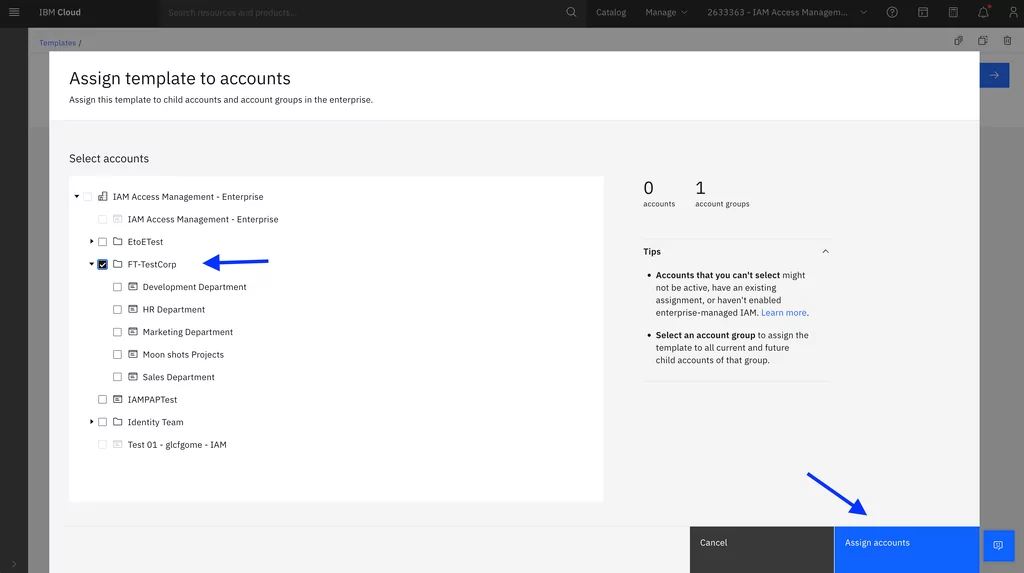
After the assignment is complete, the members of the SRE team can log in to the accounts under the account group and have the required access to perform their duties.
As your teams and cloud workloads grow, you might need to enable the SRE team to manage other resources. In the following example, we are granting the SRE team access to manage IBM Cloudant in addition to their existing access.
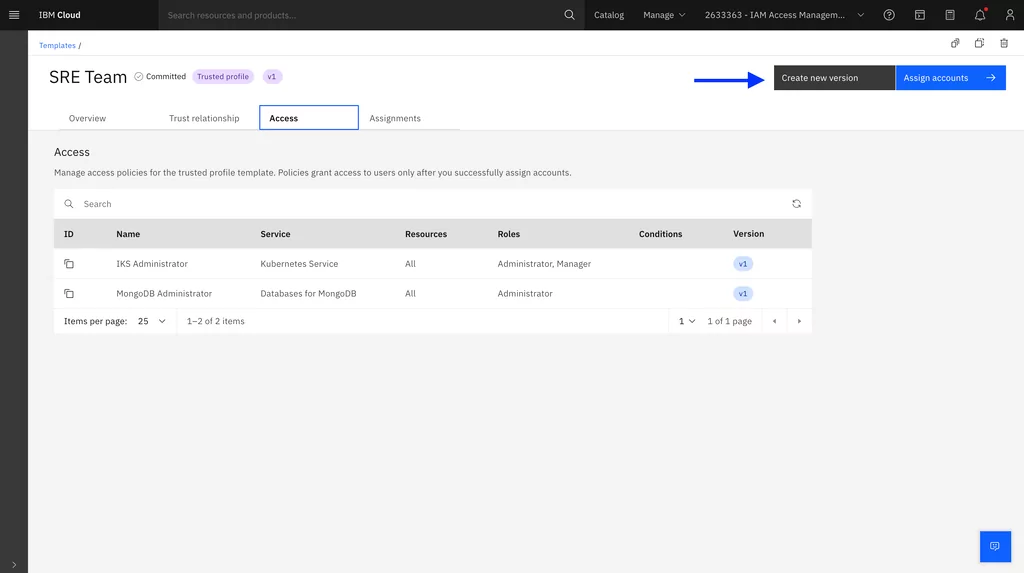
Steps to update a template and assignment
1. First, since we need to update an assigned template, we need to create a new version of the SRE team template:
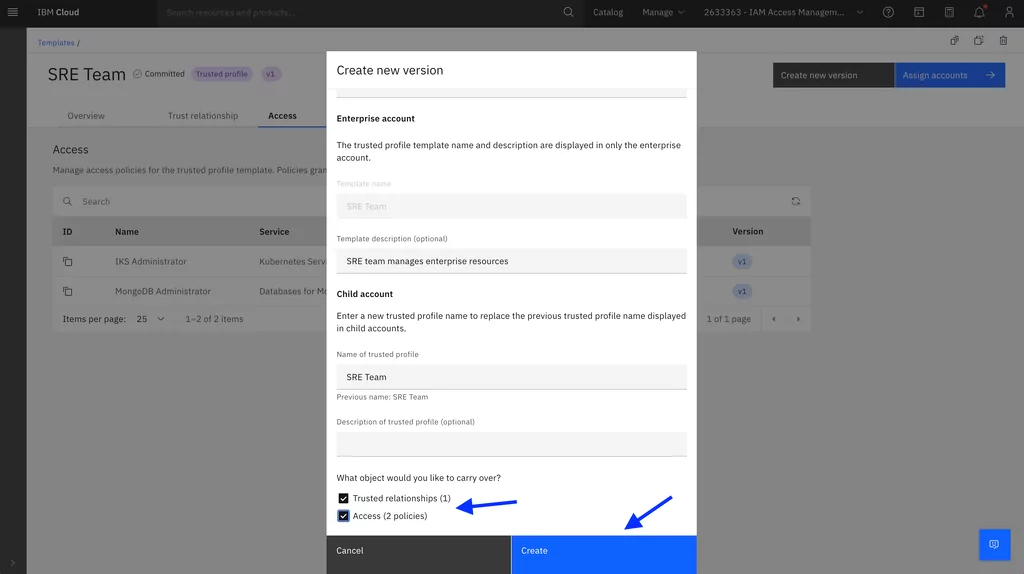
2. Since we want to expand the SRE team access, we’ll create a new policy template with access to Cloudant resources:

3. Commit the trusted profile template and policy template:
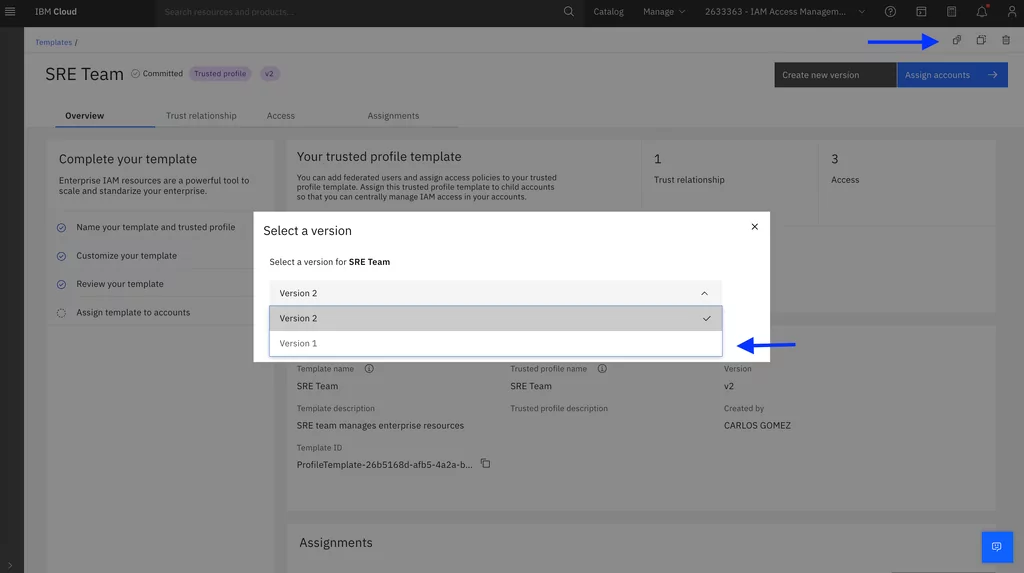
4. Now, we need to update the assignment from version 1 to version 2. First, switch to template version 1:
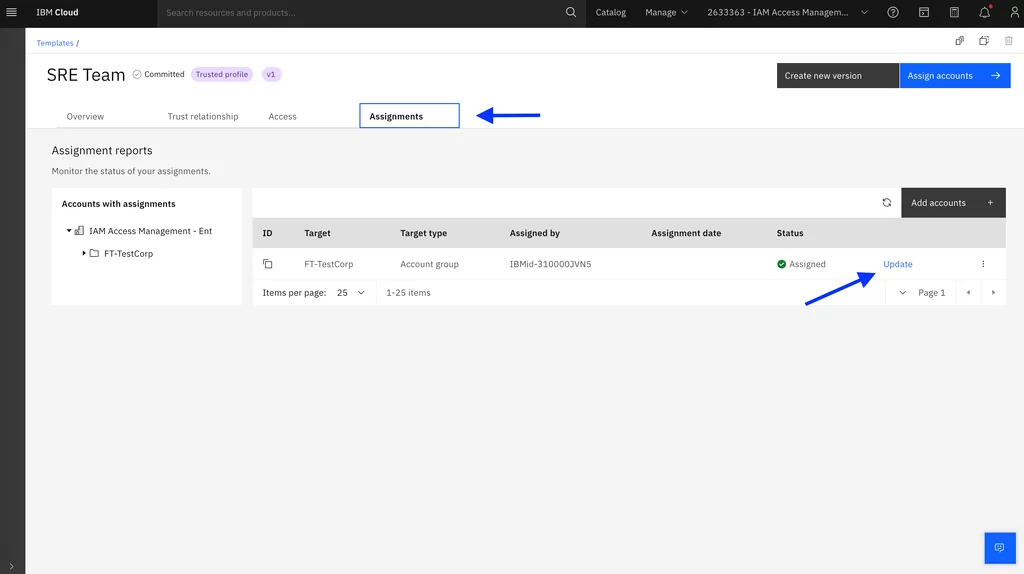
In the Assignments tab, update the assignment:
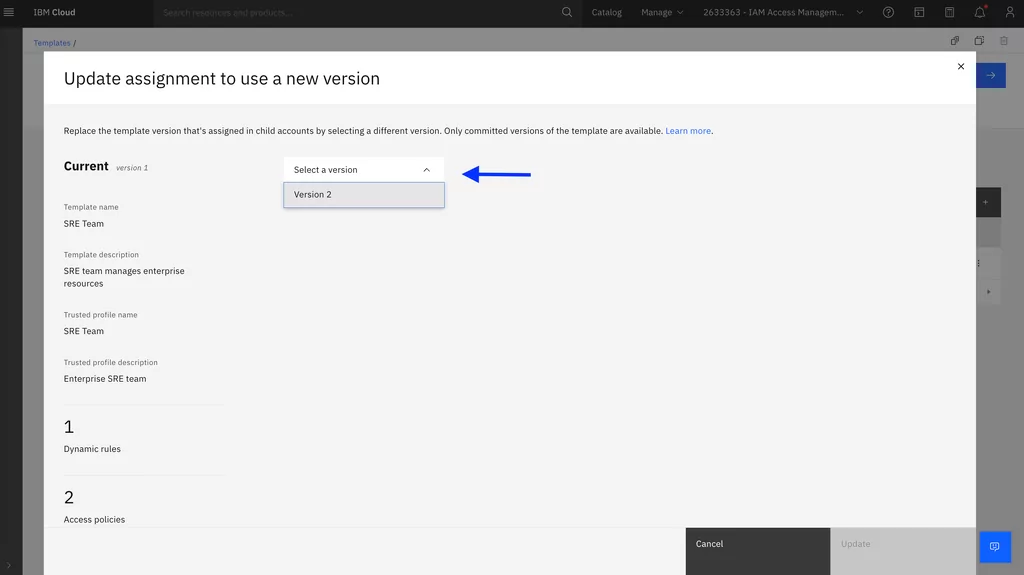
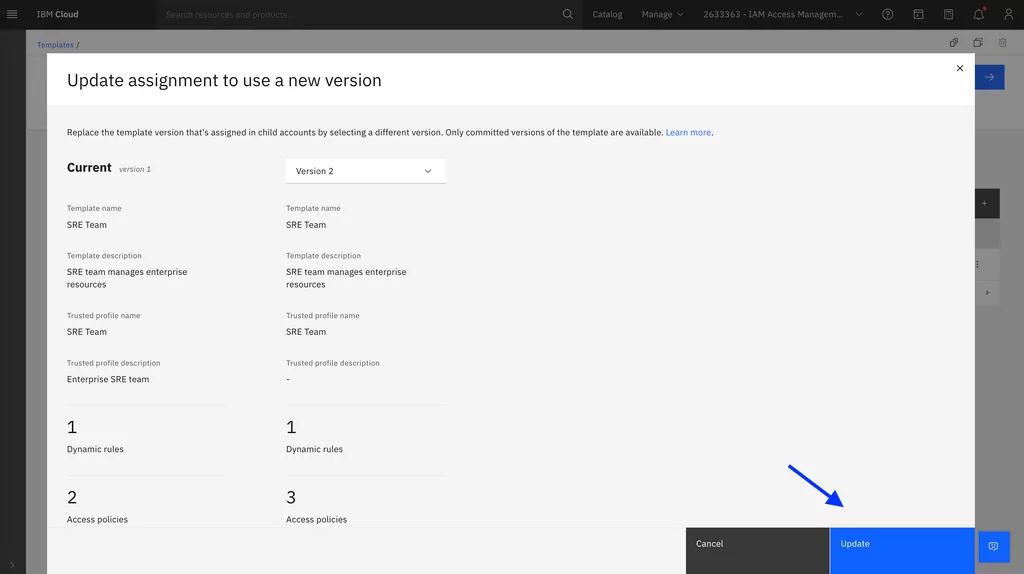
Once the assignment is complete, the SRE team will now be able to manage IBM Cloudant resources in addition to the existing IBM Cloud Kubernetes Service and IBM Cloud Databases for MongoDB access.
Conclusion
Enterprise-managed identity and access management (IAM) is a powerful solution that simplifies and centralizes access and security configuration. In this article, we explored how this approach can be a game-changer for managing access to resources across a growing number of accounts.
The challenges faced by the banking client in managing access for their SRE team across multiple accounts were complex and time-consuming. However, by leveraging enterprise-managed IAM templates, they transformed an ongoing effort into a one-time setup activity. This streamlined access provisioning and enhanced security by ensuring that access control remained consistent and enforced across accounts.
Other interface samples
Included below are the equivalent steps needed to complete this use case using the command line interface and Terraform:
Ready to simplify access management? Learn more about enterprise-managed IAM
More from Cloud

October 23, 2023
3 keys to building a robust hybrid cloud risk strategy
2 min read – Hybrid cloud has become the new normal for enterprises in nearly all industries. Many enterprises have also deployed a hybrid multicloud environment that’s reliant on an ecosystem of different cloud service providers. 71% of executives think it’s difficult to realize the full potential of a digital transformation without having a solid hybrid cloud strategy in place. [1] Managing complex business operations across a hybrid multicloud environment presents leaders with unique challenges, not least of which are cyberthreats that can bring…
<!—->

October 18, 2023
IBM Cloud Databases version End-of-Life announcement
2 min read – IBM Cloud Databases is announcing the End of Life on the following database versions on April 26, 2024: IBM Cloud Databases for MySQL v5.7 IBM Cloud Databases for Elasticsearch v7.17 IBM Cloud Databases for MongoDB v4.4 IBM Cloud Databases for Redis v5.0 IBM Cloud Databases for etcd v3.3 On April 26, 2024, support for the above versions ends. Next steps IBM recommends that customers upgrade their database deployments to the next supported version. Our recommended procedure for this is restoring…
<!—->

October 16, 2023
Living in a data sovereign world
7 min read – As the world continues to become a globally connected ecosystem, data fluidity has sparked national and international conversations around notions of data and digital sovereignty. While these concepts are still emerging, many countries are developing laws and regulations to deal with the boundless nature of data, and the global and multinational organizations that are creating, housing, and distributing them. What do organizations need to do to in order to operate under these new sovereignty concepts? First, we must understand how…
<!—->

October 16, 2023
Announcing the deprecation of prior generation Db2 Warehouse plans on AWS
2 min read – We recently launched the next generation of IBM Db2 Warehouse on AWS. This new generation brings a host of new capabilities, including support for cloud object storage (Amazon S3), open data and table formats, and integration with IBM watsonx.data. Learn more here. As a result, we will end support for the prior generation Db2 Warehouse plans on AWS. Affected plans Db2 Warehouse Flex on AWS Db2 Warehouse Flex Performance on AWS Starting today, you will no longer be able to…
<!—->
IBM Newsletters
Get our newsletters and topic updates that deliver the latest thought leadership and insights on emerging trends.
Subscribe now More newsletters
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://www.ibm.com/blog/enterprise-managed-iam-an-sre-team-case-study/



