Researchers have attributed the recent JumpCloud breach to a branch of North Korea’s Lazarus Group. Early indications suggest that the group was financially motivated, primarily targeting cryptocurrency and blockchain companies.
JumpCloud is an enterprise directory-as-a-service provider serving over 180,000 customers, according to its website, including Monday.com, GoFundMe, and others. 6sense tracks its platform as the 32nd most popular in identity and access management (IAM), with a 0.2% market share.
On July 12, JumpCloud CISO Robert Phan revealed in a blog post “a sophisticated nation-state sponsored threat actor that gained unauthorized access to our systems to target a small and specific set of our customers.” Exactly which nation-state was unclear until today, when Tom Hegel, senior threat researcher with SentinelOne, tied the hacker-controlled infrastructure to North Korea. Hegel also connected the attack with a social engineering campaign identified by Github on July 18.
Crowdstrike, working directly with JumpCloud, offered more specific attribution to Reuters today, naming a subsect of the Lazarus Group they track as “Labyrinth Chollima.”
Now, working with victims of the breach, researchers from Mandiant are filling out even more of the puzzle. In upcoming research, the cybersecurity firm plans to reveal that the hackers are primarily targeting the Web3 industry, stealing credentials from crypto and blockchain companies for follow-on attacks.
JumpCloud Breach Chronology
JumpCloud first became aware of suspicious activity on June 27, at 3:13 P.M. UTC. It occurred “on an internal orchestration system which we traced back to a sophisticated spear-phishing campaign,” Pham wrote, which began the week prior, on June 22.
The attackers had managed to reach “a specific area of our infrastructure,” Pham admitted, successfully performing a data injection attack against the company’s commands framework. To mitigate the damage, he wrote, “we rotated credentials, rebuilt infrastructure, and took a number of other actions to further secure our network and perimeter. Additionally, we activated our prepared incident response plan and worked with our Incident Response (IR) partner to analyze all systems and logs for potential activity. It was also at this time, as part of our IR plan, that we contacted and engaged law enforcement in our investigation.”
Initial evidence of customer compromise was spotted at 3:35 UTC on July 5. The company notified affected customers and, later that day, initiated a force-rotation of all administrator API keys.
JumpCloud has not yet disclosed how many customers have been affected by its breach, or how badly. Pham did note that “the attack vector used by the threat actor has been mitigated.”
How IoCs Pointed To The DPRK
JumpCloud had identified its hackers as a nation-state entity. But which one?
The evidence was in the publicly disclosed indicators of compromise (IOCs). With them, Hegel says, “I’m able to start diving into the IPs themselves, trying to understand their profile, see what else is being used on that server, what those domains are talking to.” In one case, Hegel connected an IP with a domain identified in another social engineering campaign which GitHub attributed to North Korean hackers.
Hegel slowly mapped out the attackers’ command infrastructure — an IP that related to a domain, a domain that related to a previously known cluster or attack.
The attackers left behind certain digital fingerprints like how and when it was registered, as well as “the timing of how it resolves to other servers, and other random technical characteristics like the SSL cert, or the software running on that server,” Hegel clarifies. “There are a million different attributes we can use to profile the fingerprint of a server, which, in this case, overlaps with other North Korean stuff.”
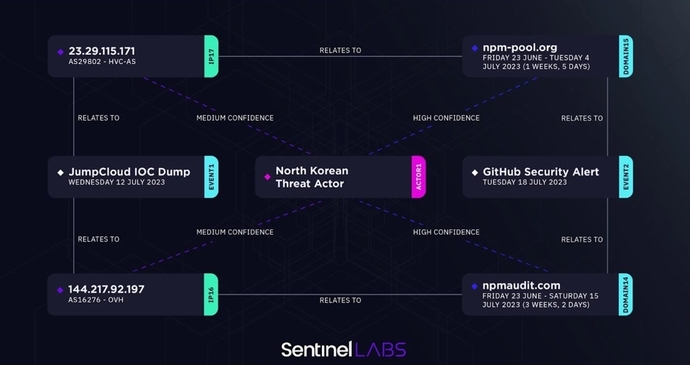
The image above charts how the two campaigns, and the various domains and IPs therein, are connected. “Clustering all that together, you’re getting an understanding that this is one big set of infrastructure. It’s all related,” Hegel explains. “And who do I see operating out of this infrastructure? At that point, we’re seeing it overlap with multiple clusters of other Lazarus campaigns.”
Targeting the Crypto Industry
As an IAM service provider, JumpCloud provides a direct path for hackers to steal credentials from companies that might prove useful for follow-on attacks. But what kind of attacks did Lazarus intend to pursue this time?
Here too, in retrospect, there were clues. Like in JumpCloud’s blog post, where Pham noted how the attack, far from a general spray-and-pray type of campaign, “was extremely targeted and limited to specific customers.”
And there was the GitHub attack to which Hegel drew a connection. In that case, “many of these targeted accounts are connected to the blockchain, cryptocurrency, or online gambling sectors,” Github noted in its blog post.
In a statement on the JumpCloud attackers shared with Dark Reading, Mandiant revealed, “with high confidence that this is a cryptocurrency-focused element within the DPRK’s Reconnaissance General Bureau (RGB), targeting companies with cryptocurrency verticals to obtain credentials and reconnaissance data,” the vendor wrote. “This is a financially motivated threat actor that we’ve seen increasingly target the cryptocurrency industry and various blockchain platforms.”
According to Austin Larsen, Mandiant senior incident response consultant with Google Cloud, Mandiant has not identified any financial consequences for the JumpCloud victims it has worked with. However, that only seems to be because “this campaign was primarily focused on obtaining credentials from priority targets and reconnaissance data for future intrusions,” he says. In at least one case, in fact, the team “identified evidence that the actor successfully completed their objective of gathering credentials from priority targets.”
North Korean hackers targeting the crypto industry to fund the Kim regime is nothing new. But the JumpCloud attack reiterates just how refined and successful their ongoing strategy has become. “They’re very creative,” Hegel thinks. “It’s really showcasing their understanding, and their desire to conduct multilevel supply chain attacks.”
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Automotive / EVs, Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- BlockOffsets. Modernizing Environmental Offset Ownership. Access Here.
- Source: https://www.darkreading.com/attacks-breaches/north-korean-attackers-targeted-crypto-companies-in-jumpcloud-breach



