![]()
SafetyDetectives Cybersecurity Team
Published on: November 20, 2023
A hacker released 1.9 million lines of data related to Turkish vaccinations, potentially exposing the information of almost 2 million citizens.
The SafetyDetectives cybersecurity team discovered a web forum post allegedly containing vaccination records from Turkey. Other forum members speculated that the information came from the 2021 e-Nabız (e-Pulse) leak involving Turkey’s Ministry of Health, but our investigation confirmed the leak to be new and presumably collected on April 4, 2023. It included vaccination data from 2015 to 2023.
The leak was shared on a web forum on September 10, 2023. It was posted in SQL format and not behind a paywall, making the full database accessible to the public. A close inspection of the data showed that it was likely collected from an online server by exploiting an information disclosure vulnerability.
Screenshot of the post sharing data of Turkish vaccinations
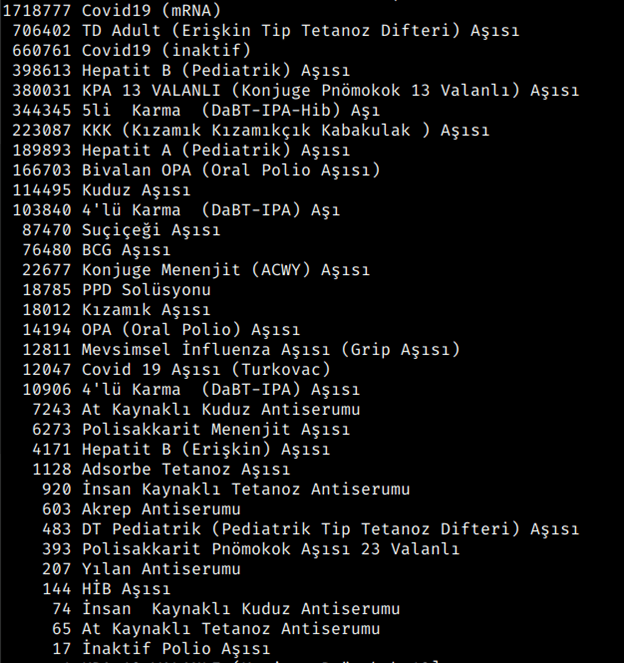
SafetyDetectives’ cybersecurity team reviewed the lines of data posted for free and identified details related to 5.3 million doses of vaccines rolled out on a national scale, with records from hospitals from various cities.
The leaked information included:
- Vaccine types received by individuals
- Dose numbers of specific vaccinations across the country
- Dates of vaccinations
- Hospitals where vaccinations were performed
- Birth dates
- Patients’ partial Turkish Identification Numbers (TCKNs for short)
- Doctors’ full TCKNs
- Other vaccination and supply chain details
Patients’ TCKNs were partially redacted, while doctors’ TCKNs were displayed in full. This might indicate that the data could possibly have been scraped from an online platform or service used by Turkish healthcare providers or the Ministry of Health. There were a total of 125,000 listed TCKNs for doctors. Considering Turkey had over 183,000 physicians in 2021, this suggests the breach might have exposed the personally identifiable information (PII) of around 70% of the doctors in the country.
Additionally, our team observed through its examination of the leak that the lines of data only included vaccine ID’s starting with “123.” Hence, we estimate that the hacker collected the information by querying specific ID numbers and that more unreleased data is available on the platform or server that was compromised.
We have sent a responsible disclosure notice to Turkey’s Ministry of Health and are awaiting their response. As of the date of publication, we cannot say whether the exploited vulnerability has been patched. We also have no means to identify who is leaking the information, nor can we confirm if the attacker has already extracted more lines of information from the database.
Below is a breakdown of the data exposed in the breach:
Potential Impacts
While names and other PII are not included in the database, the exposed national ID numbers and birth dates can be counterchecked with public records or other potential data breaches. This could give hackers a complete set of information that they could use for various fraudulent activities.
For instance, malicious actors could carry out fake financial transactions using the victims’ names, TCKNs, and birth dates — details that banks commonly require when processing requests. They could also take advantage of doctors’ TCKNs to scam patients into paying for counterfeit prescription medications or medical services.
Similarly, stolen identities could be exploited for romance scams (also known as confidence fraud), where malicious actors use bogus online personas to build fake romantic relationships with individuals whom they eventually manipulate into sending them money. For example, in 2022, Turkish neurosurgeon Dr. Kerem Bikmaz became the victim of identity theft. His photo was used in countless fake social media profiles running elaborate romance scamming operations.
Doctors in Turkey also deal with an increasing threat of physical violence, commonly due to claims of inadequate medical attention or disagreements between healthcare providers and their patients. A data leak that exposes the identities of doctors can potentially lead to more cases of direct assault. Affected physicians could also fall victim to doxing — the release of personal or sensitive information for the purposes of harassment.
What Should You Do if You Think You’re Affected?
If you are a Turkish doctor who thinks their medical records might have been compromised in the breach, reach out to your hospital or healthcare institution to discuss your concerns. The sooner information disclosure vulnerabilities are addressed, the higher the chances of preventing further leaks and minimizing further exposure.
If you see anything unusual, contact your financial institution or the local authorities to report the incident. Taking precautions can help in guarding against potential identity theft.
What Are Clearweb Leaks and Why Should You Care?
Hackers use all corners of the internet to share information, organize cyberattacks, and talk about data breaches. Some of hackers’ preferred channels are clearweb forums. These are online networks that allow users to post information about breaches and leaks. They offer anonymity to their members and have features like paywalling for users who choose to require payment from those who wish to access their shared data.
Our cybersecurity researchers scour popular data breach forums on the clearweb to find the latest cyberattacks, leaks, and breaches. We operate within legal and ethical boundaries when investigating and do not engage in, endorse, or promote illegal activities, hacking, or the unauthorized acquisition or dissemination of data.
Any references to illicit activities are for reporting purposes only, based on third-party sources or findings, and not firsthand engagements by our team.
By reporting on these incidents, we aim to proactively inform potentially affected parties earlier so that they can act quickly to protect their data. Our disclosures are rooted in meticulous research and are intended solely for informational and preventive purposes. In no way should these reports be construed as allegations, insinuations, or indicators of fault or negligence by any individual or organization.
In 2021, Brazil’s health ministry suffered a ransomware attack that compromised citizens’ vaccination data. As a result, officials had to defer the implementation of health requirements for people entering the country.
About Us
SafetyDetectives.com is the world’s largest antivirus review website. The SafetyDetectives research lab is a pro bono service that aims to help the online community defend itself against cyber threats while educating organizations on protecting their users’ data.
- SEO Powered Content & PR Distribution. Get Amplified Today.
- PlatoData.Network Vertical Generative Ai. Empower Yourself. Access Here.
- PlatoAiStream. Web3 Intelligence. Knowledge Amplified. Access Here.
- PlatoESG. Carbon, CleanTech, Energy, Environment, Solar, Waste Management. Access Here.
- PlatoHealth. Biotech and Clinical Trials Intelligence. Access Here.
- Source: https://www.safetydetectives.com/news/turkish-vaccinations-leak-report/