Read Time: 6 minutes
In the web3 world, phishing attempts come in a variety of forms. Since the technology is still developing, new kinds of attacks can arise. Some attacks, such as ice phishing, are specific to Web3, while others resemble the more common credential phishing attacks on Web2.
Before knowing what exactly an ice phishing attack is and how it works, Let’s first understand how transactions are signed in Blockchain and what are token allowance.
Signing a Transaction
We can connect to decentralized applications using wallets like Metamask to execute actions like lending, borrowing, purchasing NFT, etc. Malicious users are trying to take advantage of the fact that users must sign transactions using their Metamask to execute these acts.
The Metamask pop-up will appear and ask the user whether they want to confirm or cancel the transaction when an app has to perform an on-chain operation. See the below image.
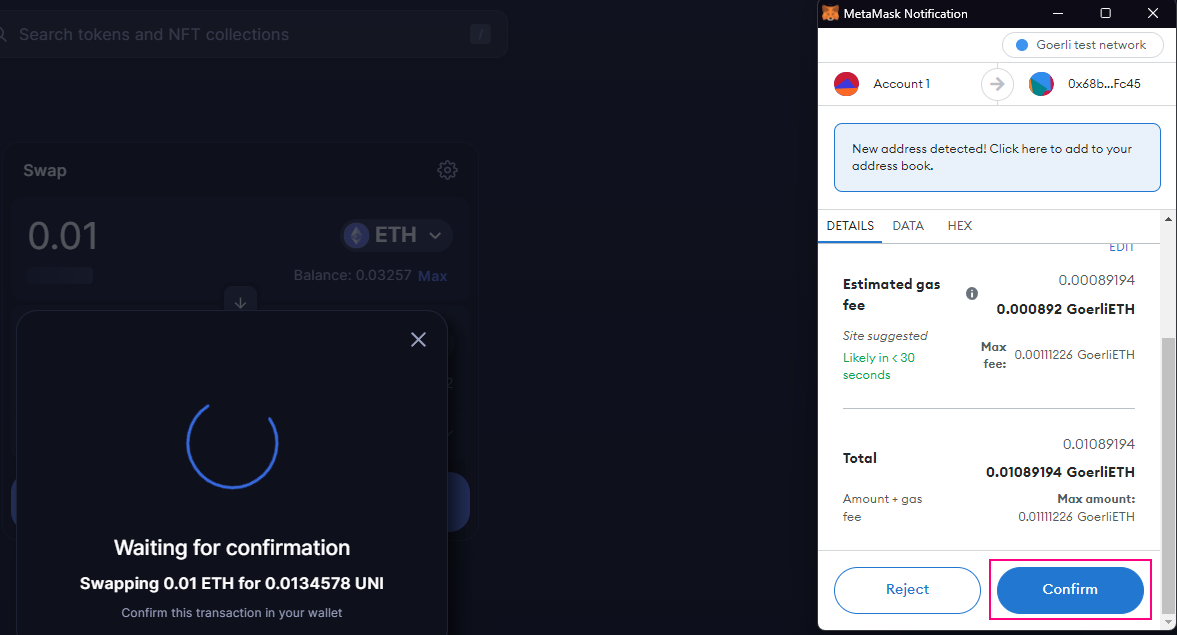
In the above example, we can see that metamask prompts us for confirmation when we are swapping ETH for UNI tokens. The transaction will be executed once we confirm it. As a result, it may be more difficult to understand what activities you permit in some transactions, particularly if we are permitting a series of acts rather than a single immediate action. Attackers are looking to exploit this lack of clarity when they go ice phishing.
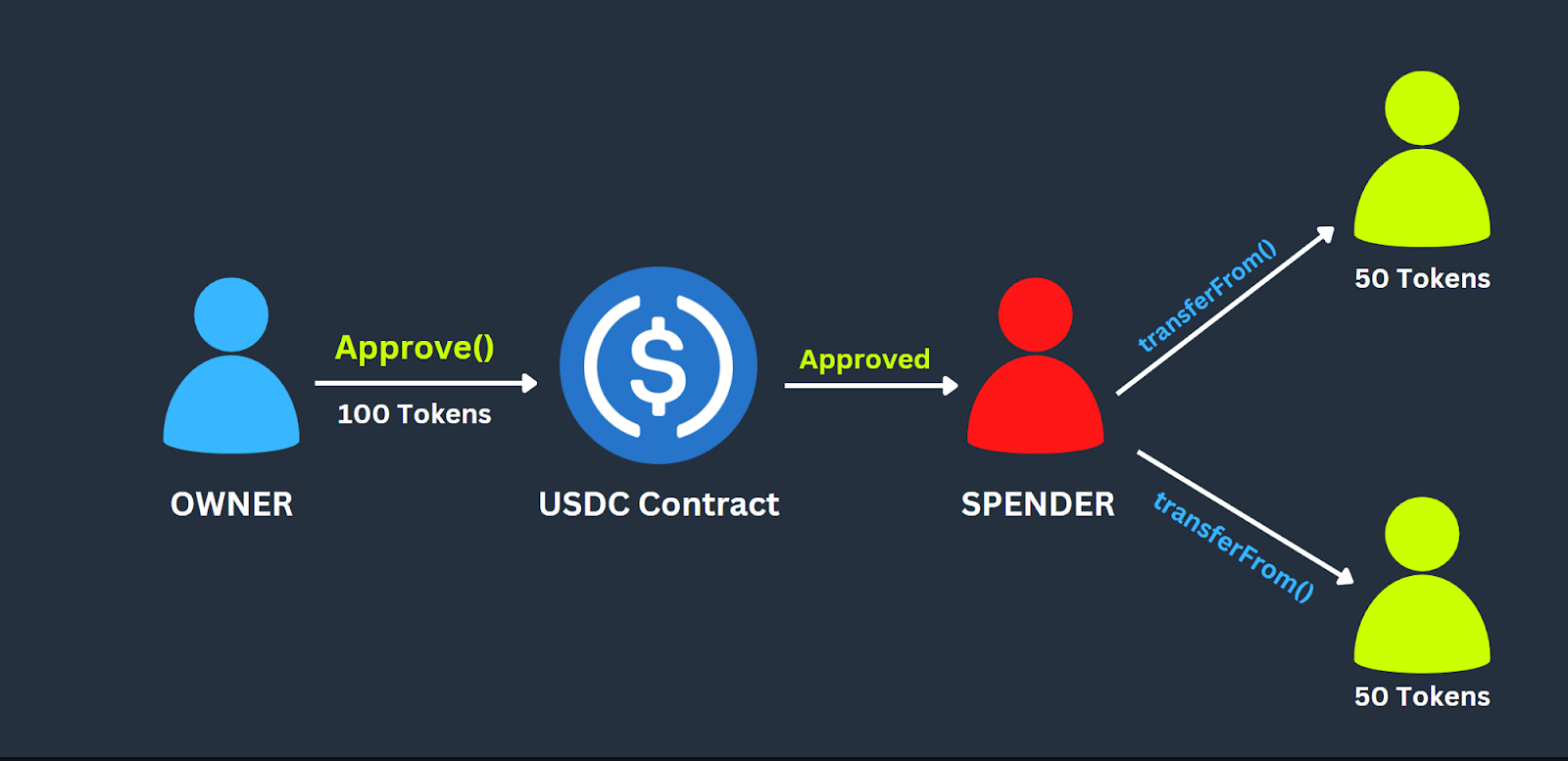
Token Allowance
A transaction in which a token owner authorizes a token spender to spend the token amount on the token owner’s behalf. An owner can provide a token allowance for non-fungible and fungible tokens. The owner is the account that owns the tokens and grants the spender the allowance.
What is Ice Phishing
In Simple terms, Ice Phishing involves tricking a user into signing a malicious transaction so the attacker can gain control over the crypto assets.
The “ice phishing” method does not involve stealing someone else’s private keys. Instead, it requires trying to trick a user into approving a transaction that grants the attacker control over the user’s tokens.
Approvals are a frequent type of transaction that allow interactions of the users with DeFi Protocols. This makes ice phishing a considerable threat to Web3 investors since interacting with DeFi protocols requires you to grant permission to interact.
How does the attack works?
The attacker executes this attack in two steps:
1. Tricking Victim into signing Approvals Transactions:
Attackers construct fraudulent websites impersonating a DEX, such as SushiSwap, or as a help page for a crypto product.
The attacker usually sends out these malicious links to promotional giveaways and “exclusive” NFTs mints, Phishing E-mails, Tweets, Discords, etc., pushing people to jump into these malicious websites by creating a false sense of urgency and provoking FOMO (fear of missing out) among users. See the Example below:
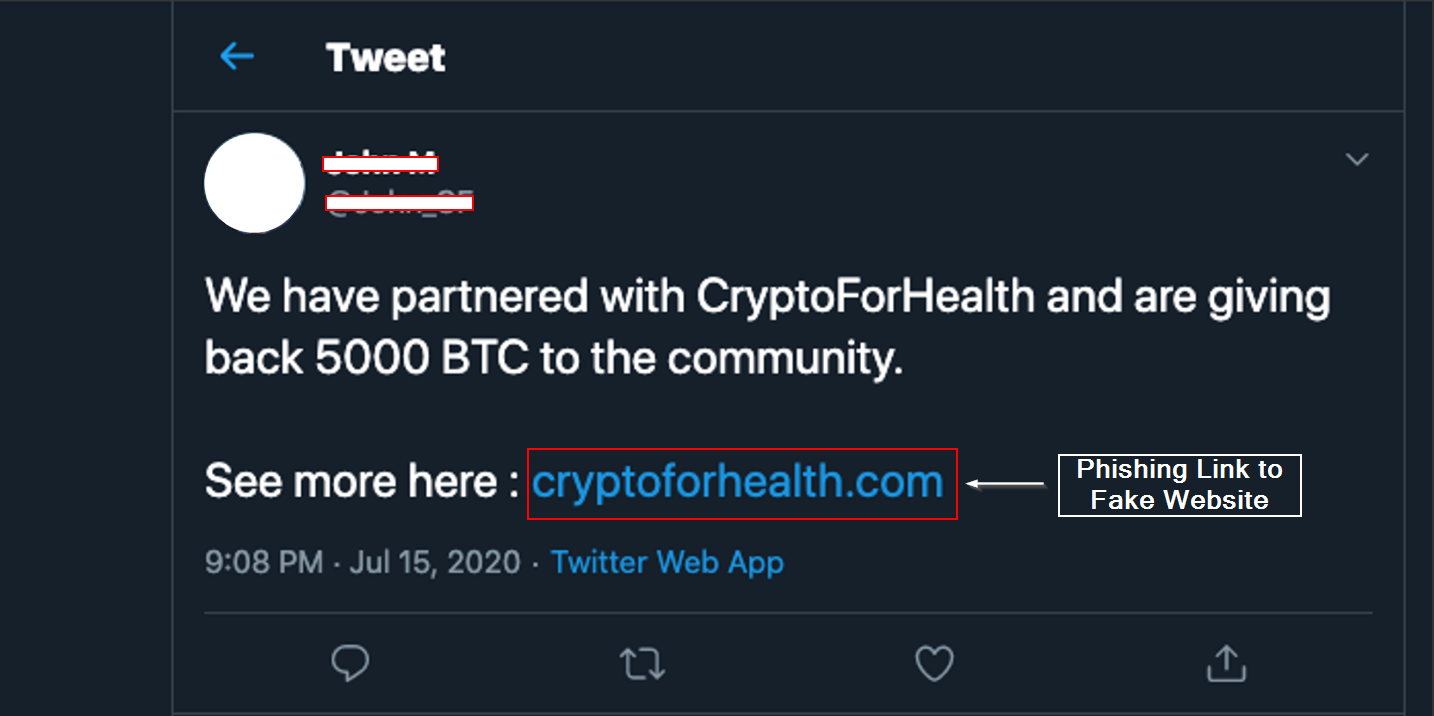
Scammers succeed when they can trick users into connecting wallets to their Malicious websites and manipulate users into signing approvals to spend their assets.
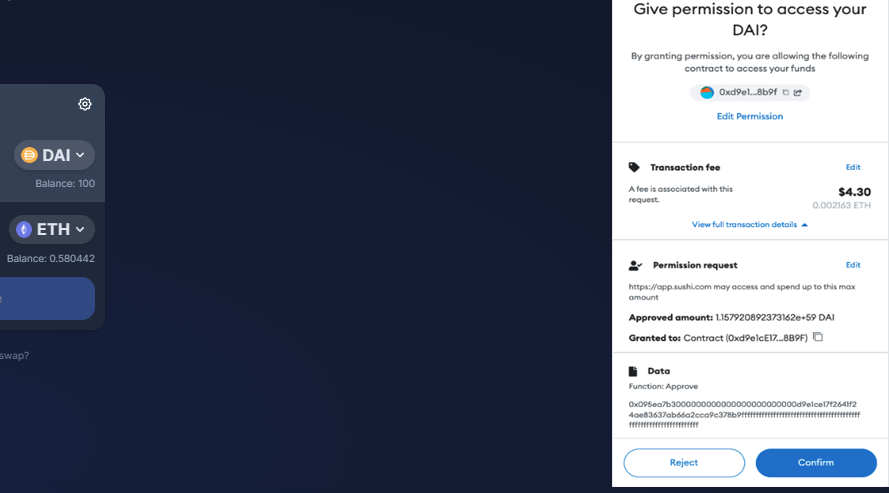
2. Stealing tokens from users’ wallets:
As soon as the user approves the tokens to the malicious attacker’s address. The attacker calls the transferFrom function and transfers all tokens to his wallet. The scam usually involves at least two wallets. Initially, the Ice Phishing wallet, which the users had given their approval, and then the Recipient wallet, where the attacker transferred the tokens.
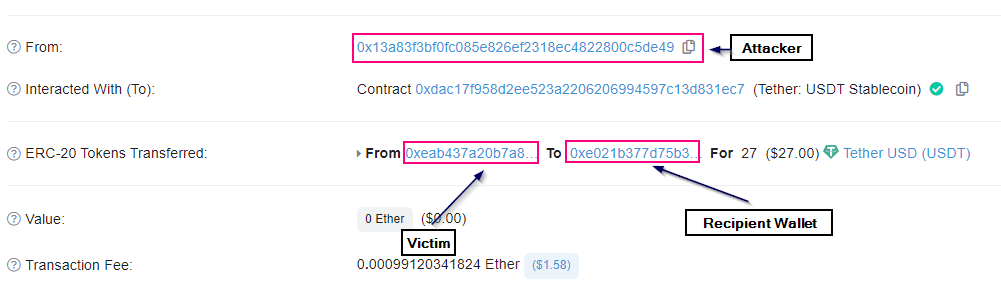
Badger DAO Case Study
Badger is a DeFi protocol that allows one to earn interest on deposits. On December 2nd, 2021, BadgerDAO was under an ice phishing attack. Badger’s Cloudflare API key was compromised, allowing the attacker to take over the front-end infrastructure.
The attacker was thus able to inject malicious script onto the front end. Now, the users tried to connect to BadgerDAO, thinking they were depositing tokens to get a yield. Still, the actual transaction they signed granted the attackers complete access to their assets.
Attackers took millions from victims’ accounts and specifically chose individuals with higher balances to target. They changed their script throughout the day in an effort to remain undetected. Eventually, BadgerDAO recognized the attack and halted the smart contract, but the exploiters had already stolen around $121 million from 200 accounts.
How to Protect Yourself
Don’t click on Suspicious Links: To avoid phishing URLs and domain squatters, only use the verified URL to access dApps and services. The project URL is usually available on their verified Twitter account if in doubt.
Verify the transaction before signing: It is essential to read the transaction’s details before signing it in Metamask or any other wallet to ensure the actions you intend will be executed.
Manage your crypto assets through multiple wallets: Distribute your cryptocurrency holdings, storing long-term investments and valuable NFTs in cold storage like hardware wallets while keeping funds for regular transactions and more active dApps in a different hot wallet.
Periodically review and revoke Allowance: Periodically review and revoke your allowances is always a good idea, especially for NFT marketplaces, whenever you are not actively using a dapp. This minimizes your chance of losing money to exploits or attacks and reduces the impact of phishing scams. You can use Revoke.cash or Etherscan token approval checker for it.
Get updated with Scams to avoid them: Keep an eye out for scams and report any unusual behaviour. Reporting scams will help the security professionals and law enforcement in catching fraudsters before they cause too much harm.
Conclusion
Ice phishing attacks and other cryptocurrency frauds will probably grow more prevalent as the crypto market continues to rise. Attention and education are the finest security precautions. Users should be aware of how these scams operate so they may take the appropriate precautions to keep themselves safe. It is always worthwhile to take an extra moment to confirm that the URL you’re interacting with has been validated both on-chain and by a reliable source.
FAQs
What should I do if I suspect an ice phishing attempt?
Check and revoke your approvals for any addresses that may have compromised your wallet. https://etherscan.io/tokenapprovalchecker. Also, transfer all your funds to other wallets.
How can I protect myself from ice phishing?
To protect yourself from ice phishing attack, you should be cautious of unsolicited emails, messages, and phone calls, even if they appear to be from a reputable source. Verify the transaction before signing it.
How to revoke approvals for an address?
You can use Revoke.cash or Etherscan token approval checker for removing approvals for an address.
8 Views
- SEO Powered Content & PR Distribution. Get Amplified Today.
- Platoblockchain. Web3 Metaverse Intelligence. Knowledge Amplified. Access Here.
- Source: https://blog.quillhash.com/2023/01/19/what-are-ice-phishing-attacks-and-how-to-avoid-getting-hooked/



