Standoff between Poly Network and Hacker over keys to multisig wallet
Aug 18 Update:
In an August 17 Medium article, the Poly Network team announced that they had offered the hacker, whom they refer to as “Mr. White Hat,” the position of Chief Security Officer along with a $500,000 bounty for identifying the exploit. In the post, the team declared they have “no intention of holding Mr. White Hat legally responsible.”
While the hacker has so far refused the position and the bounty, the ordeal is far from over. While a majority of the funds had been returned in the days following the attack, a large portion of the returned funds—about $235 million—remain in a multisig wallet under the control of Poly Network and the hacker. This means that Poly Network cannot move the funds out of this wallet without the hacker’s private keys.
Despite the hacker ignoring the $500,000 bounty offer, Poly Network decided they could still send the funds (160 ETH) to an address under the hacker’s control anyway, as disclosed in another on-chain message.

The hacker responded on-chain, challenging Poly Network’s motives and stating he is not ready to publish the private keys this week.

In their response, Poly Network stated they would still donate the 160 ETH to the hacker, continuing to plead that the hacker release the private keys as soon as possible.


On August 10, Poly Network suffered a $612 million hack—the largest crypto-related hack to date. Where the typical DeFi hack is against specific DeFi instruments, resulting in much smaller losses, in this case the attack was against Poly Network’s infrastructure, focusing on the DeFi platform itself and targeting control of the decentralized exchange’s (DEX) smart contracts What are smart contracts? A smart contract is a computer pro… More. As a result, the main cross-chain contract became completely controlled by the hacker, allowing him to unlock tokens that were supposed to be locked within the contract, send the tokens to addresses under their control, and then repeat the attack across chains.
What are smart contracts? A smart contract is a computer pro… More. As a result, the main cross-chain contract became completely controlled by the hacker, allowing him to unlock tokens that were supposed to be locked within the contract, send the tokens to addresses under their control, and then repeat the attack across chains.
How Poly Network was hacked
Poly Network acts as a cross-chain interoperability bridge to facilitate the transfer of tokens between two relatively independent blockchains. As such, one of their main Poly Network smart contracts is the bridge itself. In order for bridges between chains to act effectively (e.g. for users to be able to use the network to transfer tokens across chains), they need to maintain large sums of liquidity. Whenever a user wants to “bridge” between chains Poly Network needs to efficiently burn/mint the equivalent assets on the respective chains.
The contract that issues these cross-chain token transfers uses “keepers” to verify and execute the transactions. Once the keeper signs on the source chain the CrossChainManager contract on the destination chain will check the Keeper’s signature for validity and execute the equivalent on the destination chain to complete the “bridge”.
Since the smart contract executes the transactions and not the user themselves, the hacker was able to exploit the CrossChainManager smart contract and swap the “keepers” for a malicious keeper under their control. As a result, the main cross-chain contract on the Poly Network became completely controlled by the hacker, allowing him to unlock tokens that were supposed to remain locked within the bridge contract and move the tokens to addresses under his control. The hacker then replicated the attack across chains.
Who are the real victims of the Poly Network hack?
As a result of the hacker’s actions, users’ funds that were “locked” in these contracts suffered the true loss. While specific individuals tokens were not taken, by removing such a large amount locked in the protocol, Poly Network would no longer have the liquidity to support a large scale exodus if all users wished to pull their funds from the contracts. However, because of the decentralized nature of DeFi, the lack of any KYC processes and cross-border reach means identifying who the real victims are and where they are located is nearly impossible.
Overall, it’s a sophisticated exploit to a poorly designed smart contract, with the “risk” and “behavior” affecting the users of Poly Network. The investors are the true victims not Poly Network themselves. Arguably, Poly Network shares responsibility with the hacker by not ensuring the quality of their smart contract thereby exposing investors to significant risk.
There is currently no indication that the Poly Network code had ever received an audit. Searching through the protocol’s GitHub repos did not indicate any audits had been performed or reported.
Poly Network hacker returns the stolen funds
Much to the surprise of those monitoring the Poly Network theft, on August 11 the attacker began returning some of the stolen funds. This left many over the internet to wonder—why?
In all the swapping the hacker has done in an effort to obfuscate their trail, it appears the hacker had at one point reused a wallet that already had previous transactions with some prominent exchanges that could have identifying “know your customer” (KYC) information on him.
There are claims of the hacker potentially being a white hat, given the returning of funds. However, it is extremely unlikely that a white hat would have taken the same steps to attempt to obfuscate the funds trail if they had always intended on returning the money.
At the time of this blog, CipherTrace has confirmed nearly all funds have been returned to Poly Network into the addresses they had developed specifically for the hacker to return the funds. These addresses are:
- 0x71Fb9dB587F6d47Ac8192Cd76110E05B8fd2142f
- 0xEEBb0c4a5017bEd8079B88F35528eF2c722b31fc
- 0xA4b291Ed1220310d3120f515B5B7AccaecD66F17
Funds frozen August 10 (day of hack)
$33M USDT frozen
Funds returned August 11
Poly contract: $85 million USDC
BSC contract: $256.2 million in 3 major tokens (mostly BTCB, Binance pegged ETH, BUSD) and $2.637 million in BNB
Ethereum contract: $3.4 million in SHIB, renBTC, and Fei
Funds returned August 12
Ethereum contract: $96.9 in DAI, $47.8 in WBTC, $93M in ETH
The repercussions of such a large DeFi hack
Lawmakers will expedite implementation of DeFi regulations, especially as the number of DeFi hacks spirals, as epitomized by this latest Poly Network hack. Ultimately, regulators are likely to classify decentralized exchanges (DEXs) as virtual asset service providers (VASPs) in accordance with the FATF’s recommendations. FinCEN is likely to classify DEXs as Money Service Businesses (MSBs), which means DEXs and other DeFi applications will be required to meet anti-money laundering (AML) and KYC obligations. I would also expect the CFTC to regulate DeFi communities and the SEC to regulate DeFi securities regulations.
In addition smart contract quality standards will become more rigorous, audit standards will emerge. Further, the DeFi “insurance market” will evolve and mature that can adequately evaluate and under right DeFi technical risks.
DeFi hacks approach $2 billion for the year—what’s next?
This hack exemplifies the importance of smart contract security and audit standards to assure the quality and reduce vulnerabilities in the code.
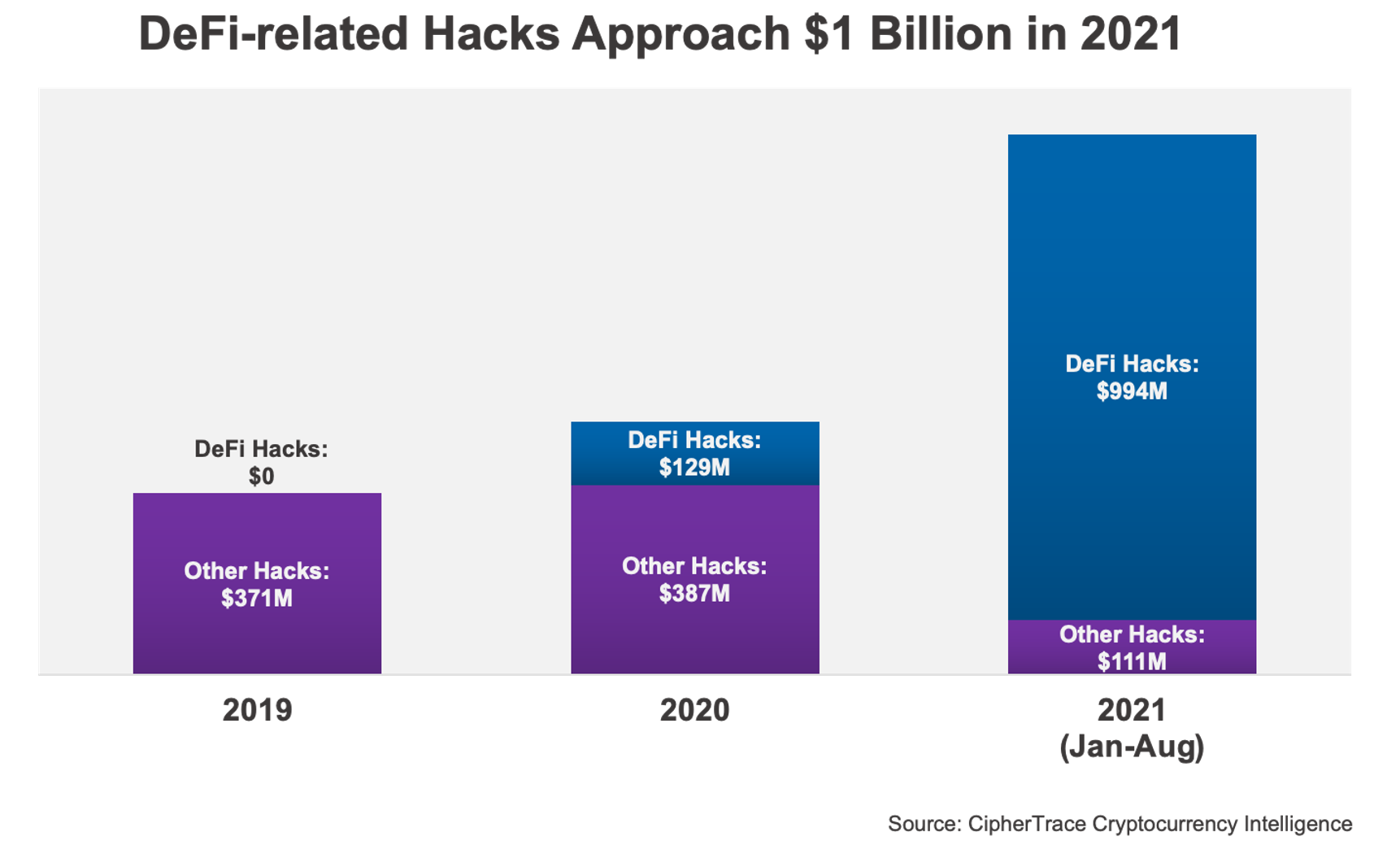
According to our latest Cryptocurrency Crime and Anti-Money Laundering Report, by the end of August the DeFi-hack volume netted by criminals in 2021 make up $361 million. Today this number has nearly tripled as DeFi hacks now make up $994 million, making up 90% of all of 2021’s hack volume which tops just over $1.1 billion.
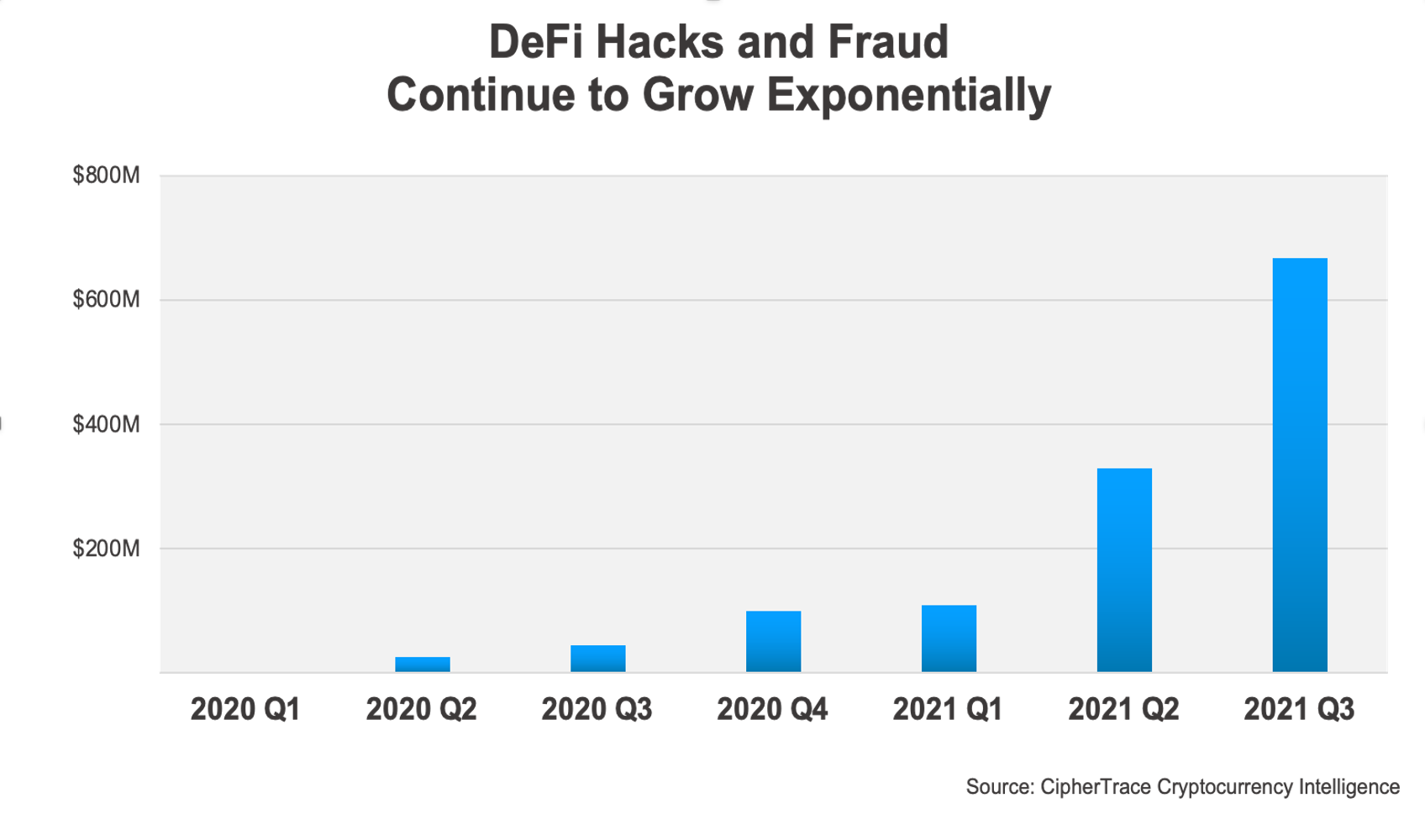 As DeFi hacks and fraud continue to grow exponentially quarter over quarter, the future of DeFi crime appears grim if the trend is to continue. If DeFi crimes continue to grow more sophisticated, as previewed by the Poly Network hack, smart contracts are likely to be increasingly targeted for larger scale attacks.
As DeFi hacks and fraud continue to grow exponentially quarter over quarter, the future of DeFi crime appears grim if the trend is to continue. If DeFi crimes continue to grow more sophisticated, as previewed by the Poly Network hack, smart contracts are likely to be increasingly targeted for larger scale attacks.
Appendix
On August 11 the hacker held an “on-chain” Q&A. The following can be viewed by decoding the input data on some of his transactions.
Q & A, PART ONE:
Q: WHY HACKING?
A: FOR FUN 🙂
Q: WHY POLY NETWORK?
A: CROSS CHAIN HACKING IS HOT
Q: WHY TRANSFERING TOKENS?
A: TO KEEP IT SAFE.
WHEN SPOTTING THE BUG, I HAD A MIXED FEELING. ASK YOURSELF WHAT TO DO HAD YOU FACING SO MUCH FORTUNE. ASKING THE PROJECT TEAM POLITELY SO THAT THEY CAN FIX IT? ANYONE COULD BE THE TRAITOR GIVEN ONE BILLION! I CAN TRUST NOBODY! THE ONLY SOLUTION I CAN COME UP WITH IS SAVING IT IN A _TRUSTED_ ACCOUNT WHILE KEEPING MYSELF _ANONYMOUS_ AND _SAFE_.
NOW EVERYONE SMELLS A SENSE OF CONSPIRACY. INSIDER? NOT ME, BUT WHO KNOWS? I TAKE THE RESPOSIBILITY TO EXPOSE THE VULNERABILITY BEFORE ANY INSIDERS HIDING AND EXPLOITING IT!
Q: WHY SO SOPHISTICATED?
A: THE POLY NETWORK IS DECENT SYSTEM. IT’S ONE OF THE MOST CHALLENGING ATTACKS THAT A HACKER CAN ENJOY. AND I HAD TO BE QUICK TO BEAT ANY INSIDERS OR HACKERS, I TOOK IT AS A BONUS CHALL 🙂
Q: ARE YOU EXPOSED?
A: NO. NEVER. I UNDERSTOOD THE RISK OF EXPOSING MYSELF EVEN IF I DON’T DO EVIL. SO I USED TEMPORARY EMAIL, IP OR _SO CALLED_ FINGERPRINT, WHICH WERE UNTRACABLE. I PREFER TO STAY IN THE DARK AND SAVE THE WORLD.
https://etherscan.io/tx/0x1fb7d1054df46c9734be76ccc14fa871b6729e33b98f9a3429670d27ec692bc0
Q & A, PART TWO:
Q: WHAT REALLY HAPPENED 30 HOURS AGO?
A: LONG STORY.
BELIEVE IT OR NOT, I WAS _FORCED_ TO PLAY THE GAME.
THE POLY NETWORK IS A SOPHISTICATED SYSTEM, I DIDN’T MANAGE TO BUILD A LOCAL TESTING ENVIRONMENT. I FAILED TO PRODUCE A POC AT THE BEGINNING. HOWEVER, THE AHA MOMEMNT CAME JUST BEFORE I WAS TO GIVE UP. AFTER DEBUGGING ALL NIGHT, I CRAFTED A _SINGLE_ MESSAGE TO THE ONTOLOGY NETWORK.
I WAS PLANNING TO LAUNCH A COOL BLITZKRIEG TO TAKE OVER THE FOUR NETWORK: ETH, BSC, POLYGON & HECO. HOWEVER THE HECO NETWORK GOES WRONG! THE RELAYER DOES NOT BEHAVE LIKE THE OTHERS, A KEEPER JUST RELAYED MY EXPLOIT DIRECTLY, AND THE KEY WAS UPDATED TO SOME WRONG PARAMETERS. IT RUINED MY PLAN.
I SHOULD HAVE STOPPED AT THAT MOMENT, BUT I DECIDED TO LET THE SHOW GO ON! WHAT IF THEY PATCH THE BUG SECRETLY WITHOUT ANY NOTIFICATION?
HOWEVER, I DIDN’T WANT TO CAUSE _REAL_ PANIC OF THE CRYPTO WORLD. SO I CHOSE TO IGNORE SHIT COINS, SO PEOPLE DIDN’T HAVE TO WORRY ABOUT THEM GOING TO ZERO. I TOOK IMPORTANT TOKENS (EXCEPT FOR SHIB) AND DIDN’T SELL ANY OF THEM.
Q: THEN WHY SELLING/SWAPPING THE STABLES?
A: I WAS PISSED BY THE POLY TEAM FOR THEIR INITIAL REPONSE.
THEY URGED OTHERS TO BLAME & HATE ME BEFORE I HAD ANY CHANCE TO REPLY! OF COURSE I KNEW THERE ARE FAKE DEFI COINS, BUT I DIDN’T TAKE IT SERIOUSLY SINCE I HAD NO PLAN LAUNDERING THEM.
IN THE MEANWHILE, DEPOSITING THE STABLES COULD EARN SOME INTEREST TO COVER POTENTIAL COST SO THAT I HAVE MORE TIME TO NEGOTIATE WITH THE POLY TEAM.
https://etherscan.io/tx/0xd4ee4807c07702a3202f45666983855d7fa22eb1c230e4c1e840fc9389e54729
Q & A, PART THREE:
Q: WHY TIPPING 13.37?
A: I FEELED THE WARMTH FROM THE ETHEREUM COMMUNITY.
I WAS BUSY INVESTIGATING ISSUES FROM HECO AND DEBUGGING MY SCRIPTS. I THOUGHT IT WERE NETWORKING ISSUES WHY I COULD NOT DEPOSIT (I WAS BEHIND A SOPHISTICATED PROXY). SO I SHARED MY GOODWILL THE GUY.
Q: WHY ASKING TORNADO AND DAO?
A: HAVING WITNESSED SO MANY HACKINGS, I KNEW DEPOSITING INTO TORNADO IS A WISE BUT DESPERATE DECISION. IT WAS AGAINST MY ORIGINAL INTENTION. BEING THE CROWDSOURCED HACKER WAS JUST MY BAD JOKE AFTER MEETING SO MANY BEGGARS 🙂
Q: WHY RETURNING?
A: THAT’S ALWAYS THE PLAN! I AM _NOT_ VERY INTERESTED IN MONEY!I KNOW IT HURTS WHEN PEOPLE ARE ATTACKED, BUT SHOULDN’T THEY LEARN SOMETHING FROM THOSE HACKS? I ANNOUNCED THE RETURNING DECISION BEFORE MIDNIGHT SO PEOPLE WHO HAD FAITH IN ME SHOULD HAD A GOOD REST 😉
Q: WHY RETURNING SLOWLY?
A: I DO NEED TIME TO TALK WITH THE POLY TEAM. SORRY, IT’S THE ONLY WAY I KNOW TO PROVE MY DIGNITY WHILE HIDING MYSELF IDENTITY. AND I NEED SOME REST.
Q: THE POLY TEAM?
A: I ALREADY STARTED TALKING WITH THEM BRIEFLY, THE LOGS ARE ON THE ETHEREUM. I MAY OR MAY NOT PUBLISH THEM. THE PAINS THEY HAVE SUFFERED IS TEMPORARY BUT MEMORABLE.
I WOULD LIKE TO GIVE THEM TIPS ON HOW TO SECURE THEIR NETWORKS,SO THAT THEY CAN BE ELIGIBLE TO MANAGE THE BILLION PROJECT IN THE FUTURE. THE POLY NETWORK IS A WELL DESIGNED SYSTEM AND IT WILL HANDLE MORE ASSETS. THEY HAVE GOT A LOT OF NEW FOLLOWERS ON TWITTER, RIGHT?
https://etherscan.io/tx/0xe954bed9abc08c20b8e4241c5a9e69ed212759152dd588bb976b47eca353a5bc
Value taken from Poly Network Hack
| Chain | TX Hash | asset | amount | $value |
| BSC | 0x534966864bda354628d4f1c66db45cbefcdda7433e9576e7664fea01bb05be9a | BNB | 6,613.44 | $2,460,861.21 |
| BSC | 0xd59223a8cd2406cfd0563b16e06482b9a3efecfd896d590a3dba1042697de11a | USDC | 87,603,373.77 | $87,624,502.53 |
| BSC | 0x4e57f59395aca4847c4d001db4a980b92aab7676bc0e2d57ee39e83502527d6c | ETH | 26,629.16 | $85,896,083.66 |
| BSC | 0x50105b6d07b4d738cd11b4b8ae16943bed09c7ce724dc8b171c74155dd496c25 | BTCB | 1,023.88 | $47,427,704.52 |
| BSC | 0xd65025a2dd953f529815bd3c669ada635c6001b3cc50e042f9477c7db077b4c9 | BUSD | 32,107,854.11 | $32,124,918.14 |
| BSC | 0xea37b320843f75a8a849fdf13cd357cb64761a848d48a516c3cac5bbd6caaad5 | USDC | 298.9405633 | $299.04 |
| ETH | 0xad7a2c70c958fcd3effbf374d0acf3774a9257577625ae4c838e24b0de17602a | ETH | 2,857.49 | $8,977,279.13 |
| ETH | 0x5a8b2152ec7d5538030b53347ac82e263c58fe7455695543055a2356f3ad4998 | USDC | 96,389,444.23 | $96,430,660.58 |
| ETH | 0x3f55ff1fa4eb3437afe42f4fea57903e8e663bc3b17cb982f1c8d4c8f03a2083 | WBTC | 1,032.12 | 46,971,609.47 |
| ETH | 0xa7c56561bbe9fbd48e2e26306e5bb10d24786504833103d3f023751bbcc8a3d9 | DAI | 673,227.94 | $673.628.12 |
| ETH | 0xc917838cc3d1edd871c1800363b4e4a8eaf8da2018e417210407cc53f94cd44e | UNI | 43,023.75 | $1,242,040.44 |
| ETH | 0xe05dcda4f1b779989b0aa2bd3fa262d4e6e13343831cb337c2c5beb2266138f5 | SHIB | 259,737,345,149.52 | $1,974,082.34 |
| ETH | 0xb12681d9e91e69b94960611b227c90af25e5352881907f1deee609b8d5e94d7d | renBTC | 14.47265047 | $659,141.75 |
| ETH | 0x06aca16c483c3e61d5cdf39dc34815c29d6672a77313ec36bf66040c256a7db3 | USDT | 33,431,197.73 | $33,391,733.96 |
| ETH | 0xc797aa9d4714e00164fcac4975d8f0a231dae6280458d78382bd2ec46ece08e7 | WETH | 26,109.06 | $82,052,128.62 |
| ETH | 0xd8c1f7424593ddba11a0e072b61082bf3d931583cb75f7843fc2a8685d20033a | FEI | 616,082.59 | $616,082.59 |
| Poly | 0x1d260d040f67eb2f3e474418bf85cc50b70101ca2473109fa1bf1e54525a3e01 | USDC | 85,089,610.91 | $85,061,020.80 |
| Poly | 0xfbe66beaadf82cc51a8739f387415da1f638d0654a28a1532c6333feb2857790 | USDC | 108.694578 | $108.66 |
Poly Network Hacker Addresses
Poly Network publicly identified three addresses allegedly controlled by the attacker:
- 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963 (ETH)
- 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71 (BSC)
- 0x5dc3603C9D42Ff184153a8a9094a73d461663214 (POLYGON)
PlatoAi. Web3 Reimagined. Data Intelligence Amplified.
Click here to access.
Source: https://ciphertrace.com/poly-network-suffers-largest-crypto-hack-ever-recorded/



