One of the biggest obstacles for fulfilling the promise of smart-home technology has been lack of consumer confidence in device security. Smart-home devices are perceived to operate like the lawless Wild West. A smartphone manufacturer with billions in brand equity will tightly follow recognised security practices. However, a little-known Wi-Fi camera maker might cut corners to reduce cost and time to market, says Kevin Wirick, VP of CommScope SentryDevice Security.
The lack of a rigorous, requisite level of cyber defense for all smart-home products has led to disturbing stories of IoT breaches that erode consumer confidence. These incidents range from hacked baby monitors to the theft of a casino’s high-roller database by using the smart thermostat in an aquarium as a network entry point.
These issues and the complexity of smart-home technology, which has been built on many competing platforms and protocols, have kept it from living up to its adoption promise. Until now.
Unifying standard
Matter 1.0 is the new unifying standard for interoperability and security among smart-home devices. Announced late last year, the spec and certification programme are the result of a collaboration involving 550 technology companies under the auspices of the Connectivity Standards Alliance (CSA). Amazon, Apple, Google, and Samsung are among the many collaborators.
Matter’s primary objectives are to make smart-home devices interoperable while improving and standardising security across suppliers and IoT ecosystems. Any device with the Matter logo becomes identifiable as a secure device. The standard simplifies buying, installation and management for consumers and provides security peace of mind, motivating them to move ahead with building or expanding their smart-home networks.
For IoT device makers, Matter eliminates the need to independently integrate each product they develop with multiple proprietary smart-home platforms, such as Amazon Alexa, Apple HomeKit/Siri, Google Home, and Samsung SmartThings. Instead, they can use the Matter software development kit (SDK) royalty-free to incorporate their products into the Matter ecosystem, where they interoperate with these and other Matter-compliant smart environments. Since the spec became public last fall, 285 products have been Matter-certified.
Securing Matter IoT
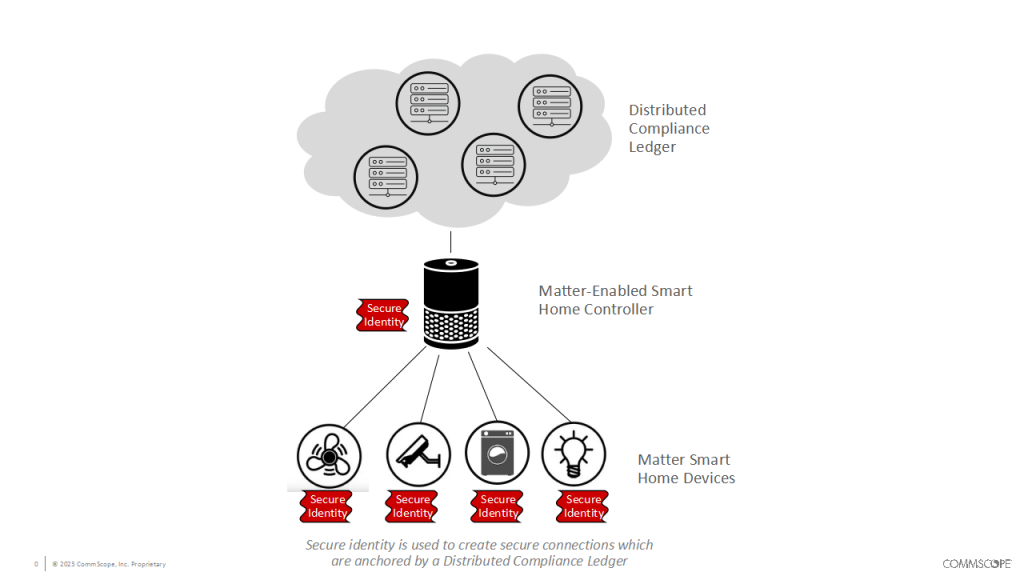
Matter defines three areas of IoT security operations. The first is verifying a device’s identity before allowing it to join a smart-home network. Just as in human communication, knowing the identity of the party with whom you’re communicating is a fundamental security requirement. Matter uses digital credentials with industry-standard public key infrastructure (PKI) technology to establish trust, much as a person uses a driver’s license or passport to establish who they are.
Second, Matter uses an encrypted key exchange to establish a secure channel between devices so that malicious actors can’t interfere with communications. This process compares trusted information in the two communicating devices and then generates new shared encryption keys to secure communications between them.
The third secure Matter operation is a public list, or ledger, that describes Matter-registered devices. Blockchain technology – the same used for cryptocurrency applications – makes the ledger secure, transparent, and traceable. It can be read by anyone but requires security credentials to write and update information about the devices in it. The ledger includes information about each smart-home product from manufacturing to certification to the firmware updates. The registry also includes a link for the download server to access the software so that security enhancements can be added once products are deployed.
By combining these three techniques – device identity, secure communications, and a distributed ledger – Matter creates a table-stakes level of rigor for smart-home device security and enables different manufacturers’ smart light switches, HVAC systems, security sensors, door locks, and other devices to work under a common security scheme, bringing order to the “Wild West” of smart-home cyber security.

IoT Security Enables Cooperation
With standardised protocols that allow diverse IoT brands to communicate with one another, Matter opens up new functionality such as cooperative automation. For example, a motion sensor made by Manufacturer A might detect when a resident arrives home and automatically activate the home’s thermostat, made by Manufacturer B, to turn on the heat or air conditioning. Or if the sensor detects that no one is home for a certain length of time, it might trigger the thermostat to adjust the temperature and also automatically shut down smart appliances like the oven and TV – potentially made by Manufacturers C and D – that shouldn’t run unattended.
In this way, Matter allows dissimilar smart devices to communicate and consumers to manage them with the voice interface of their choice. A command such as “Turn on outdoor lights,” for example, is the same for all Matter-enabled lighting, regardless of manufacturer or underlying network connection type.
In addition to improving consumer experiences, Matter enables greater efficiencies for device manufacturers. For example, they can:
- Increase production output with single-SKU products that work with all Matter-certified devices and ecosystems
- Decrease customer acquisition and support costs by simplifying smart-home setup and operations with a single application, interface, and set of commands that work across all devices
- Reduce development costs, risk, and time to market by moving from customised smart product designs to a unified, Matter-standard platform
- Free developers to focus on applications instead of system software for greater product differentiation and innovation
A Matter of getting certified
For Matter to be successful, it needs wide industry adoption. That, in turn, hinges on device manufacturers adopting Matter security standards into their product development and manufacturing security processes.
To tame the “Wild West” of potential security problems among connected devices, CSA requires that device manufacturers meet certain security standards for their digital credentials, ensuring the necessary level of trust. One of the fundamental security requirements for Matter is that a distinct digital credential must be installed on each device. Furthermore, the credential cannot be extracted, copied, or duplicated for use on multiple devices. This measure serves as a safeguard against potential security breaches to create counterfeit products. A device manufacturer can either develop their own processes to meet all the Matter security requirements for protecting and managing device credentials, or they can work with an established security company offering Matter PKI services to provide certificates and register them with the CSA.
Matter defines this digital credential as a device attestation certificate (DAC). The DAC is securely embedded in the device once it is manufactured using security technology included in all IoT silicon devices. IoT makers without the technical depth and staff resources to create certificates or use these silicon security tools can turn to a CSA-approved certificate authority management partner to obtain the DACs and integrate Matter open-source code into their devices.
Accelerated adoption


Matter is on track to accelerate smart-home adoption with interoperability and security standards that will improve consumer shopping, installation, and usage experiences while deterring hackers. ABI Research predicts that within five years, more than half of the world’s key smart home devices will ship supporting Matter. The Matter logo on products will notify consumers that the Wild West is tamed, and they can safely buy devices knowing that their homes will be secure and not be readily hacked.
More information on CommScope Sentry Matter IoT security solutions can be found here.
The author is Kevin Wirick, VP ofCommScope SentryDevice Security.
Comment on this article below or via Twitter: @IoTNow_OR @jcIoTnow
- SEO Powered Content & PR Distribution. Get Amplified Today.
- EVM Finance. Unified Interface for Decentralized Finance. Access Here.
- Quantum Media Group. IR/PR Amplified. Access Here.
- PlatoAiStream. Web3 Data Intelligence. Knowledge Amplified. Access Here.
- Source: https://www.iot-now.com/2023/06/08/131271-taming-the-wild-west-of-smart-home-security-to-enable-widespread-adoption/



